
Three-tier architecture is a well-established software application architecture that organizes applications into three logical and physical computing tiers: the presentation tier, or user interface; the application tier, where data is processed; and the data tier, where application data is stored and managed.
The chief benefit of three-tier architecture is that because each tier runs on its own infrastructure, each tier can be developed simultaneously by a separate development team. And can be updated or scaled as needed without impacting the other tiers.
For decades three-tier architecture was the prevailing architecture for client-server applications. Today, most three-tier applications are targets for modernization that uses cloud-native technologies such as containers and microservices and for migration to the cloud.
Connect and integrate your systems to prepare your infrastructure for AI.
Register for the guide on app modernization

Presentation tier
The presentation tier is the user interface and communication layer of the application, where the end user interacts with the application. Its main purpose is to display information to and collect information from the user. This top-level tier can run on a web browser, as desktop application, or a graphical user interface (GUI), for example. Web presentation tiers are developed by using HTML, CSS, and JavaScript. Desktop applications can be written in various languages depending on the platform.
Application tier
The application tier, also known as the logic tier or middle tier, is the heart of the application. In this tier, information that is collected in the presentation tier is processed - sometimes against other information in the data tier - using business logic, a specific set of business rules. The application tier can also add, delete, or modify data in the data tier.
The application tier is typically developed by using Python, Java, Perl, PHP or Ruby, and communicates with the data tier by using API calls.
The data tier, sometimes called database tier, data access tier or back-end, is where the information that is processed by the application is stored and managed. This can be a relational database management system such as PostgreSQL , MySQL, MariaDB, Oracle, Db2, Informix or Microsoft SQL Server, or in a NoSQL Database server such as Cassandra, CouchDB , or MongoDB .
In a three-tier application, all communication goes through the application tier. The presentation tier and the data tier cannot communicate directly with one another.
Tier versus layer
In discussions of three-tier architecture, layer is often used interchangeably – and mistakenly – for tier , as in 'presentation layer' or 'business logic layer'.
They aren't the same. A 'layer' refers to a functional division of the software, but a 'tier' refers to a functional division of the software that runs on infrastructure separate from the other divisions. The Contacts app on your phone, for example, is a three - layer application, but a single-tier application, because all three layers run on your phone.
The difference is important because layers can't offer the same benefits as tiers.
Again, the chief benefit of three-tier architecture is its logical and physical separation of functionality. Each tier can run on a separate operating system and server platform - for example, web server, application server, database server - that best fits its functional requirements. And each tier runs on at least one dedicated server hardware or virtual server, so the services of each tier can be customized and optimized without impacting the other tiers.
Other benefits (compared to single- or two-tier architecture) include:
- Faster development : Because each tier can be developed simultaneously by different teams, an organization can bring the application to market faster. And programmers can use the latest and best languages and tools for each tier.
- Improved scalability : Any tier can be scaled independently of the others as needed.
- Improved reliability : An outage in one tier is less likely to impact the availability or performance of the other tiers.
- Improved security : Because the presentation tier and data tier can't communicate directly, a well-designed application tier can function as an internal firewall, preventing SQL injections and other malicious exploits.
In web development, the tiers have different names but perform similar functions:
- The web server is the presentation tier and provides the user interface. This is usually a web page or website, such as an ecommerce site where the user adds products to the shopping cart, adds payment details or creates an account. The content can be static or dynamic, and is developed using HTML, CSS, and JavaScript.
- The application server corresponds to the middle tier, housing the business logic that is used to process user inputs. To continue the ecommerce example, this is the tier that queries the inventory database to return product availability, or adds details to a customer's profile. This layer often developed using Python, Ruby, or PHP and runs a framework such as Django, Rails, Symphony, or ASP.NET.
- The database server is the data or backend tier of a web application. It runs on database management software, such as MySQL, Oracle, DB2, or PostgreSQL.
While three-tier architecture is easily the most widely adopted multitier application architecture, there are others that you might encounter in your work or your research.
Two-tier architecture
Two-tier architecture is the original client-server architecture, consisting of a presentation tier and a data tier; the business logic lives in the presentation tier, the data tier or both. In two-tier architecture the presentation tier - and therefore the end user - has direct access to the data tier, and the business logic is often limited. A simple contact management application, where users can enter and retrieve contact data, is an example of a two-tier application.
N-tier architecture
N-tier architecture - also called or multitier architecture - refers to any application architecture with more than one tier. But applications with more than three layers are rare because extra layers offer few benefits and can make the application slower, harder to manage and more expensive to run. As a result, n-tier architecture and multitier architecture are usually synonyms for three-tier architecture.
Move to cloud faster with IBM Cloud Pak solutions running on Red Hat OpenShift software—integrated, open, containerized solutions certified by IBM®.
Seamlessly modernize your VMware workloads and applications with IBM Cloud.
Modernize, build new apps, reduce costs, and maximize ROI.
IBM Consulting® application modernization services, which are powered by IBM Consulting Cloud Accelerator, offers skills, methods, tools, and initiatives that help determine the right strategy based on your portfolio. To modernize and containerize legacy system applications and accelerate the time-to-value of hybrid cloud environments.
Discover what application modernization is, the common benefits and challenges, and how to get started.
Learn about how relational databases work and how they compare to other data storage options.
Explore cloud native applications and how they drive innovation and speed within your enterprise.
Modernize your legacy three-tier applications on your journey to cloud. Whether you need assistance with strategy, processes, or capabilities—or want full-service attention—IBM can help. Start using containerized middleware that can run in any cloud—all bundled in IBM Cloud Paks.
Presentation Domain Data Layering
26 August 2015
Martin Fowler
team organization
encapsulation
application architecture
web development
One of the most common ways to modularize an information-rich program is to separate it into three broad layers: presentation (UI), domain logic (aka business logic), and data access. So you often see web applications divided into a web layer that knows about handling HTTP requests and rendering HTML, a business logic layer that contains validations and calculations, and a data access layer that sorts out how to manage persistent data in a database or remote services.
On the whole I've found this to be an effective form of modularization for many applications and one that I regularly use and encourage. It's biggest advantage (for me) is that it allows me to reduce the scope of my attention by allowing me to think about the three topics relatively independently. When I'm working on domain logic code I can mostly ignore the UI and treat any interaction with data sources as an abstract set of functions that give me the data I need and update it as I wish. When I'm working on the data access layer I focus on the details of wrangling the data into the form required by my interface. When I'm working on the presentation I can focus on the UI behavior, treating any data to display or update as magically appearing by function calls. By separating these elements I narrow the scope of my thinking in each piece, which makes it easier for me to follow what I need to do.
This narrowing of scope doesn't imply any sequence to programming them - I usually find I need to iterate between the layers. I might build the data and domain layers off my initial understanding of the UX, but when refining the UX I need to change the domain which necessitates a change to the data layer. But even with that kind of cross-layer iteration, I find it easier to focus on one layer at a time as I make changes. It's similar to the switching of thinking modes you get with refactoring's two hats .
Another reason to modularize is to allow me to substitute different implementations of modules. This separation allows me to build multiple presentations on top of the same domain logic without duplicating it. Multiple presentations could be separate pages in a web app, having a web app plus mobile native apps, an API for scripting purposes, or even an old fashioned command line interface. Modularizing the data source allows me to cope gracefully with a change in database technology, or to support services for persistence that may change with little notice. However I have to mention that while I often hear about data access substitution being a driver for separating the data source layer, I rarely hear of someone actually doing it.
Modularity also supports testability, which naturally appeals to me as a big fan of SelfTestingCode . Module boundaries expose seams that are good affordance for testing . UI code is often tricky to test, so it's good to get as much logic as you can into a domain layer which is easily tested without having to do gymnastics to access the program through a UI 1 . Data access is often slow and awkward, so using TestDoubles around the data layer often makes domain logic testing much easier and responsive.
1: A PageObject is also an important tool to help testing around UIs.
While substitutability and testability are certainly benefits of this layering, I must stress that even without either of these reasons I would still divide into layers like this. The reduced scope of attention reason is sufficient on its own.
When talking about this we can either look at it as one pattern (presentation-domain-data) or split it into two patterns (presentation-domain, and domain-data). Both points of view are useful - I think of presentation-domain-data as a composite of presentation-domain and domain-data.
I consider these layers to be a form of module, which is a generic word I use for how we clump our software into relatively independent pieces. Exactly how this corresponds to code depends on the programming environment we're in. Usually the lowest level is some form of subroutine or function. An object-oriented language will have a notion of class that collects functions and data structure. Most languages have some form of higher level called packages or namespaces, which often can be formed into a hierarchy. Modules may correspond to separately deployable units: libraries, or services, but they don't have to.
Layering can occur at any of these levels. A small program may just put separate functions for the layers into different files. A larger system may have layers corresponding to namespaces with many classes in each.
I've mentioned three layers here, but it's common to see architectures with more than three layers. A common variation is to put a service layer between the domain and presentation, or to split the presentation layer into separate layers with something like Presentation Model . I don't find that more layers breaks the essential pattern, since the core separations still remain.
The dependencies generally run from top to bottom through the layer stack: presentation depends on the domain, which then depends on the data source. A common variation is to arrange things so that the domain does not depend on its data sources by introducing a mapper between the domain and data source layers. This approach is often referred to as a Hexagonal Architecture .
These layers are logical layers not physical tiers. I can run all three layers on my laptop, I can run the presentation and domain model in a desktop with a database on a server, I can split the presentation with a rich client in the browser and a Backed For Frontend on the server. In that case I treat the BFF as a presentation layer as it's focused on supporting a particular presentation option.
Although presentation-domain-data separation is a common approach, it should only be applied at a relatively small granularity. As an application grows, each layer can get sufficiently complex on its own that you need to modularize further. When this happens it's usually not best to use presentation-domain-data as the higher level of modules. Often frameworks encourage you to have something like view-model-data as the top level namespaces; that's OK for smaller systems, but once any of these layers gets too big you should split your top level into domain oriented modules which are internally layered.
Developers don't have to be full-stack but teams should be.
One common way I've seen this layering lead organizations astray is the AntiPattern of separating development teams by these layers. This looks appealing because front-end and back-end development require different frameworks (or even languages) making it easy for developers to specialize in one or the other. Putting those people with common skills together supports skill sharing and allows the organization to treat the team as a provider of a single, well-delineated type of work. In the same way, putting all the database specialists together fits in with the common centralization of databases and schemas. But the rich interplay between these layers necessitates frequent swapping between them. This isn't too hard when you have specialists in the same team who can casually collaborate, but team boundaries add considerable friction, as well as reducing an individual's motivation to develop the important cross-layer understanding of a system. Worse, separating the layers into teams adds distance between developers and users. Developers don't have to be full-stack (although that is laudable) but teams should be.
Further Reading
I've written about this separation from a number of different angles elsewhere. This layering drives the structure of P of EAA and chapter 1 of that book talks more about this layering. I didn't make this layering a pattern in its own right in that book but have toyed with that territory with Separated Presentation and PresentationDomainSeparation .
For more on why presentation-domain-data shouldn't be the highest level modules in a larger system, take a look at the writing and speaking of Simon Brown . I also agree with him that software architecture should be embedded in code.
I had a fascinating discussion with my colleague Badri Janakiraman about the nature of hexagonal architectures. The context was mostly around applications using Ruby on Rails, but much of the thinking applies to other cases when you may be considering this approach.
Acknowledgements
Application Layer vs. Presentation Layer
What's the difference.
The Application Layer and Presentation Layer are both layers in the OSI model that are responsible for different functions in the communication process. The Application Layer is responsible for providing network services to applications and end-users, while the Presentation Layer is responsible for translating data into a format that can be easily understood by the receiving application. While the Application Layer focuses on the actual communication between applications, the Presentation Layer focuses on the formatting and encryption of data to ensure secure and efficient transmission. Both layers work together to ensure that data is transmitted accurately and securely across a network.
Further Detail
Introduction.
When it comes to the OSI (Open Systems Interconnection) model, the Application Layer and Presentation Layer are two crucial components that play a significant role in ensuring smooth communication between different systems. While both layers are essential for the overall functioning of a network, they have distinct attributes that set them apart. In this article, we will delve into the characteristics of the Application Layer and Presentation Layer, highlighting their differences and similarities.
Application Layer
The Application Layer is the topmost layer in the OSI model and is responsible for providing network services to user applications. This layer serves as the interface between the user and the network, allowing users to access network resources and services. One of the key functions of the Application Layer is to establish communication between different applications running on different devices. This layer also handles tasks such as data encryption, authentication, and data compression to ensure secure and efficient communication.
Another important aspect of the Application Layer is that it defines the protocols that applications use to communicate with each other. These protocols include HTTP, FTP, SMTP, and DNS, among others. Each protocol has its specific purpose and set of rules that govern how data is transmitted between applications. The Application Layer ensures that these protocols are implemented correctly, enabling seamless communication between applications across the network.
Furthermore, the Application Layer is responsible for data formatting and presentation. It ensures that data is formatted in a way that is understandable to the receiving application. This includes tasks such as converting data into the appropriate format, handling data structures, and managing data integrity. By performing these functions, the Application Layer ensures that data is transmitted accurately and efficiently between applications.
In summary, the Application Layer plays a crucial role in facilitating communication between user applications and the network. It provides services such as data encryption, authentication, and data formatting, ensuring secure and efficient communication. By defining protocols and handling data presentation, the Application Layer enables seamless communication between applications running on different devices.
Presentation Layer
The Presentation Layer is the sixth layer in the OSI model and is responsible for translating data into a format that is understandable by the application layer. This layer focuses on data representation and ensures that data is presented in a consistent and meaningful way. One of the key functions of the Presentation Layer is data encryption and decryption, which helps secure data transmission over the network.
Another important aspect of the Presentation Layer is data compression. This layer compresses data before transmission to reduce bandwidth usage and improve network performance. By compressing data, the Presentation Layer can optimize network resources and ensure faster data transmission between devices. Additionally, the Presentation Layer handles tasks such as data translation, character encoding, and data encryption, ensuring that data is transmitted accurately and efficiently.
Furthermore, the Presentation Layer is responsible for data formatting and syntax. It ensures that data is presented in a format that is consistent and understandable by the receiving application. This includes tasks such as converting data into the appropriate format, handling data structures, and managing data integrity. By performing these functions, the Presentation Layer ensures that data is transmitted accurately and efficiently between applications.
In summary, the Presentation Layer plays a crucial role in translating data into a format that is understandable by the application layer. It focuses on data representation, data compression, and data encryption, ensuring secure and efficient data transmission over the network. By handling data formatting and syntax, the Presentation Layer enables seamless communication between applications running on different devices.
While the Application Layer and Presentation Layer have distinct functions, they share some similarities in terms of their role in the OSI model. Both layers are responsible for ensuring secure and efficient communication between applications running on different devices. They handle tasks such as data encryption, data formatting, and data presentation, ensuring that data is transmitted accurately and efficiently.
One key difference between the Application Layer and Presentation Layer is their focus on different aspects of data transmission. The Application Layer focuses on providing network services to user applications and defining protocols for communication, while the Presentation Layer focuses on translating data into a format that is understandable by the application layer. Despite these differences, both layers work together to facilitate communication between applications across the network.
Another difference between the Application Layer and Presentation Layer is their position in the OSI model. The Application Layer is the topmost layer in the OSI model, while the Presentation Layer is the sixth layer. This difference in position reflects their respective roles in the network architecture and highlights the importance of each layer in ensuring smooth communication between different systems.
In conclusion, the Application Layer and Presentation Layer are two essential components of the OSI model that play a crucial role in facilitating communication between applications running on different devices. While they have distinct functions and focus on different aspects of data transmission, both layers work together to ensure secure and efficient communication across the network. By understanding the attributes of the Application Layer and Presentation Layer, network administrators can optimize network performance and enhance the overall user experience.
Comparisons may contain inaccurate information about people, places, or facts. Please report any issues.
OSI Model: The 7 Layers of Networking Simplified
What is the OSI Model?
In the world of networking, communication between devices is the backbone of our digital age. Ever wondered how your computer sends an email, or how your smartphone streams a video seamlessly? The answer lies in a fundamental concept called the OSI model.
The OSI model, short for Open Systems Interconnection model , is a conceptual framework used to understand and standardize how different network systems communicate. Developed in 1984 by the International Organization for Standardization (ISO), it helps break down complex communication processes into simpler parts. This model is vital for IT professionals, network engineers, and anyone interested in understanding how data flows through a network.
The OSI model provides a universal way for different systems to communicate, regardless of their underlying technology. Think of it like a blueprint or a guidebook for communication. It helps manufacturers, developers, and engineers design products and services that can work together seamlessly.
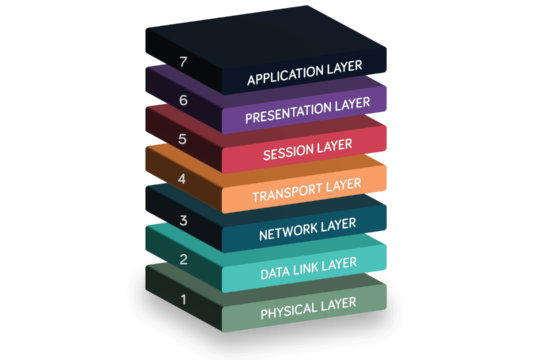
The OSI model is divided into seven layers , each responsible for a specific aspect of network communication. Each layer interacts with the one above and below it, creating a smooth flow of information. These layers, in order from top to bottom, are:
- Application Layer
- Presentation Layer
- Session Layer
- Transport Layer
- Network Layer
- Data Link Layer
- Physical Layer
Understanding these layers is key to diagnosing network issues, designing efficient networks, and ensuring secure data transmission.
Layer 1: The Physical Layer
The Physical Layer is the foundation of the OSI model. It deals with the physical connections and hardware that transmit data. This layer handles the actual signals, cables, and frequencies used to transfer data between devices.
Responsibilities:
- Defines the types of cables, connectors, and transmission mediums (e.g., copper wires, fiber optic cables, radio waves).
- Manages electrical signals and voltage levels.
- Ensures data is transmitted as bits (1s and 0s).
When you plug an Ethernet cable into your laptop, you're interacting with the Physical Layer. The cable carries electrical signals that represent your data.
Layer 2: The Data Link Layer
The Data Link Layer ensures reliable data transfer between two directly connected devices. It’s responsible for organizing bits into frames and detecting errors during transmission.
- Provides error detection and correction.
- Manages Media Access Control (MAC) addresses.
- Divides data into frames for transmission.
Your Wi-Fi router’s MAC address helps ensure that data reaches the correct device in your home network.
The Data Link Layer has two sublayers:
- Logical Link Control (LLC) – Handles error checking and frame synchronization.
- Media Access Control (MAC) – Manages access to the physical medium.
Layer 3: The Network Layer
The Network Layer is responsible for determining the best path for data to travel across networks. It uses logical addressing (like IP addresses) to identify and route packets to their destination.
- Manages IP addressing and routing.
- Determines the optimal path for data delivery.
- Handles packet forwarding and fragmentation.
When you send an email, the Network Layer ensures that the email packets travel through the internet and reach the recipient's IP address.
Common protocols used in this layer include Internet Protocol (IP) and Routing Information Protocol (RIP) .
Layer 4: The Transport Layer
The Transport Layer guarantees reliable data transfer between devices. It breaks data into smaller segments, ensures these segments arrive in order, and retransmits any lost data.
- Provides end-to-end communication.
- Manages error recovery and data flow control.
- Ensures data integrity through segmentation and reassembly.
When you download a file, the Transport Layer ensures all parts of the file arrive correctly. If a part is missing, it requests a retransmission.
Key protocols in this layer include Transmission Control Protocol (TCP) and User Datagram Protocol (UDP) .
Layer 5: The Session Layer
The Session Layer manages and controls communication sessions between devices. A session is like a conversation—it starts, continues, and ends.
- Establishes, manages, and terminates sessions.
- Handles dialog control (who talks when).
- Synchronizes data streams.
When you log in to a video conferencing app, the Session Layer manages the session between you and the other participants.
Layer 6: The Presentation Layer
The Presentation Layer focuses on data format and encryption. It ensures that data sent by one device can be read by another, regardless of format differences.
- Translates data between different formats.
- Encrypts and decrypts data for secure transmission.
- Compresses data to reduce file size.
When you open a JPEG image or play an MP3 file, the Presentation Layer converts the data into a readable format.
Layer 7: The Application Layer
The Application Layer is the closest layer to end-users. It provides network services directly to applications, allowing users to interact with data and networks.
- Interfaces with software applications.
- Provides services like email, file transfer, and web browsing.
- Manages user authentication and privacy.
When you use a web browser to visit a website, you’re interacting with the Application Layer through protocols like HTTP (Hypertext Transfer Protocol) .
Why is the OSI Model Important?
The OSI model helps simplify networking concepts by dividing them into manageable layers. This model benefits IT professionals by:
- Troubleshooting Networks : Identifying which layer is causing an issue speeds up troubleshooting.
- Standardizing Communication : Ensuring different systems and technologies can work together.
- Designing Efficient Networks : Making it easier to plan and build reliable networks.
OSI Model vs. TCP/IP Model
The TCP/IP model is another popular framework used for networking. While the OSI model has seven layers, the TCP/IP model has only four:
- Application Layer (Combines OSI’s Application, Presentation, and Session Layers)
- Internet Layer (Equivalent to OSI’s Network Layer)
- Network Interface Layer (Combines OSI’s Data Link and Physical Layers)
The OSI model is more detailed and conceptual, while the TCP/IP model is practical and widely implemented in real-world networking.
The OSI model is a powerful tool for understanding network communication. Its seven layers provide a structured approach to designing, troubleshooting, and securing networks. Whether you’re a beginner learning the basics or an IT professional managing complex networks, the OSI model offers valuable insights into how data travels from point A to point B.
Next time you send an email, browse a website, or stream a video, remember that the OSI model is working behind the scenes to make it all possible!
Datacenters.com Technology
Datacenters.com is the fastest and easiest way for businesses to find and compare solutions from the world's leading providers of Cloud , Bare Metal , and Colocation . We offer customizable RFPs, instant multicloud and bare metal deployments , and free consultations from our team of technology experts. With over 10 years of experience in the industry, we are committed to helping businesses find the right provider for their unique needs.
Download Resources
- All Resources
Top Services
- Data Center Locations
- Colocation RFP
- Bare Metal RFP
- Bare Metal IaaS
- Deploy Multicloud
- Colocation Marketplace
Latest Posts

13 Dec 2024

11 Dec 2024

Trending Posts

15 Oct 2020

29 Aug 2019

11 May 2023
Subscribe to Our Newsletter to Receive All Posts in Your Inbox!
- Engineering Mathematics
- Discrete Mathematics
- Operating System
- Computer Networks
- Digital Logic and Design
- C Programming
- Data Structures
- Theory of Computation
- Compiler Design
- Computer Org and Architecture
Presentation Layer in OSI model
Prerequisite : OSI Model
Introduction : Presentation Layer is the 6th layer in the Open System Interconnection (OSI) model. This layer is also known as Translation layer, as this layer serves as a data translator for the network. The data which this layer receives from the Application Layer is extracted and manipulated here as per the required format to transmit over the network. The main responsibility of this layer is to provide or define the data format and encryption. The presentation layer is also called as Syntax layer since it is responsible for maintaining the proper syntax of the data which it either receives or transmits to other layer(s).
Functions of Presentation Layer :
The presentation layer, being the 6th layer in the OSI model, performs several types of functions, which are described below-
- Presentation layer format and encrypts data to be sent across the network.
- This layer takes care that the data is sent in such a way that the receiver will understand the information (data) and will be able to use the data efficiently and effectively.
- This layer manages the abstract data structures and allows high-level data structures (example- banking records), which are to be defined or exchanged.
- This layer carries out the encryption at the transmitter and decryption at the receiver.
- This layer carries out data compression to reduce the bandwidth of the data to be transmitted (the primary goal of data compression is to reduce the number of bits which is to be transmitted).
- This layer is responsible for interoperability (ability of computers to exchange and make use of information) between encoding methods as different computers use different encoding methods.
- This layer basically deals with the presentation part of the data.
- Presentation layer, carries out the data compression (number of bits reduction while transmission), which in return improves the data throughput.
- This layer also deals with the issues of string representation.
- The presentation layer is also responsible for integrating all the formats into a standardized format for efficient and effective communication.
- This layer encodes the message from the user-dependent format to the common format and vice-versa for communication between dissimilar systems.
- This layer deals with the syntax and semantics of the messages.
- This layer also ensures that the messages which are to be presented to the upper as well as the lower layer should be standardized as well as in an accurate format too.
- Presentation layer is also responsible for translation, formatting, and delivery of information for processing or display.
- This layer also performs serialization (process of translating a data structure or an object into a format that can be stored or transmitted easily).
Features of Presentation Layer in the OSI model: Presentation layer, being the 6th layer in the OSI model, plays a vital role while communication is taking place between two devices in a network.
List of features which are provided by the presentation layer are:
- Presentation layer could apply certain sophisticated compression techniques, so fewer bytes of data are required to represent the information when it is sent over the network.
- If two or more devices are communicating over an encrypted connection, then this presentation layer is responsible for adding encryption on the sender’s end as well as the decoding the encryption on the receiver’s end so that it can represent the application layer with unencrypted, readable data.
- This layer formats and encrypts data to be sent over a network, providing freedom from compatibility problems.
- This presentation layer also negotiates the Transfer Syntax.
- This presentation layer is also responsible for compressing data it receives from the application layer before delivering it to the session layer (which is the 5th layer in the OSI model) and thus improves the speed as well as the efficiency of communication by minimizing the amount of the data to be transferred.
Working of Presentation Layer in the OSI model : Presentation layer in the OSI model, as a translator, converts the data sent by the application layer of the transmitting node into an acceptable and compatible data format based on the applicable network protocol and architecture. Upon arrival at the receiving computer, the presentation layer translates data into an acceptable format usable by the application layer. Basically, in other words, this layer takes care of any issues occurring when transmitted data must be viewed in a format different from the original format. Being the functional part of the OSI mode, the presentation layer performs a multitude (large number of) data conversion algorithms and character translation functions. Mainly, this layer is responsible for managing two network characteristics: protocol (set of rules) and architecture.
Presentation Layer Protocols : Presentation layer being the 6th layer, but the most important layer in the OSI model performs several types of functionalities, which makes sure that data which is being transferred or received should be accurate or clear to all the devices which are there in a closed network. Presentation Layer, for performing translations or other specified functions, needs to use certain protocols which are defined below –
- Apple Filing Protocol (AFP): Apple Filing Protocol is the proprietary network protocol (communications protocol) that offers services to macOS or the classic macOS. This is basically the network file control protocol specifically designed for Mac-based platforms.
- Lightweight Presentation Protocol (LPP): Lightweight Presentation Protocol is that protocol which is used to provide ISO presentation services on the top of TCP/IP based protocol stacks.
- NetWare Core Protocol (NCP): NetWare Core Protocol is the network protocol which is used to access file, print, directory, clock synchronization, messaging, remote command execution and other network service functions.
- Network Data Representation (NDR): Network Data Representation is basically the implementation of the presentation layer in the OSI model, which provides or defines various primitive data types, constructed data types and also several types of data representations.
- External Data Representation (XDR): External Data Representation (XDR) is the standard for the description and encoding of data. It is useful for transferring data between computer architectures and has been used to communicate data between very diverse machines. Converting from local representation to XDR is called encoding, whereas converting XDR into local representation is called decoding.
- Secure Socket Layer (SSL): The Secure Socket Layer protocol provides security to the data that is being transferred between the web browser and the server. SSL encrypts the link between a web server and a browser, which ensures that all data passed between them remains private and free from attacks.


Similar Reads
- Computer Network Tutorial A computer network is a collection of computers or devices connected to share resources. Any device which can share or receive the data is called a Node. Through which the information or data propagate is known as channels, It can be guided or unguided. In this Computer network tutorial, you’ll lear 8 min read
Basics of Computer Network
- Basics of Computer Networking Computer networking is very important in modern technology, enabling the interconnected systems that power the Internet, business communications, and everyday digital interactions. Understanding the fundamentals of computer networking is essential for anyone involved in technology, from enthusiasts 14 min read
- Introduction to basic Networking Terminology For a specific purpose if things are connected together, are referred to as a NETWORK. A network can be of many types, like a telephone network, television network, computer network, or even a people network. Similarly, a COMPUTER NETWORK is also a kind of setup, where it connects two or more device 4 min read
- Goals of Networks Computer Network means an interconnection of autonomous (standalone) computers for information exchange. The connecting media could be a copper wire, optical fiber, microwave, or satellite. Networking Elements - The computer network includes the following networking elements: At least two computers 4 min read
- Basic Characteristics of Computer Networks Computer networks allow multiple devices to connect and share resources like files, printers, and internet access. Key characteristics include the network's size (like local or wide area), the way data is transferred (wired or wireless), and the network's layout (such as star or mesh). These feature 5 min read
- Challenges of Computer Network In the age of Internet where everyone loves to work with their computers and smart phones it is impossible to think any work without networking. With advancement of technology use of computer networking is increasing rapidly. In general if we will see, we can feel also how important networking is th 4 min read
- Physical Components of Computer Network The physical components of a computer network include hardware devices and media that enable connectivity and data exchange between devices. The server, client, peer, transmission media, and connecting devices make up the hardware components. A computer network is made up of several computers connec 6 min read
Network Hardware and Software
- Types of Computer Networks A computer network is a cluster of computers over a shared communication path that works to share resources from one computer to another, provided by or located on the network nodes. In this article, we will discuss computer networks and their types. What is a Computer Network?A computer network is 11 min read
- LAN Full Form A Local area network (LAN) is a network that is used to link devices in a single office, building, or campus of up to a short distance. LAN is restricted in size. In LAN networks internet speed is from 10 Mbps to 100 Mbps (But now much higher speeds can be achieved). The most common topologies used 10 min read
- How to Set Up a LAN Network? LAN (Local Area Network) is a data communication network that locally connects network devices such as workstations, servers, routers, etc. to share the resources within a small area such as a building or campus. Physical or wireless connections are set up between workstations to share the resources 4 min read
- MAN Full Form in Computer Networking A Metropolitan Area Network (MAN) is a type of computer network that spans over a metropolitan area, typically a city. It provides high-speed data communication services such as video, audio, and data transfer between multiple LANs (Local Area Networks) and WANs (Wide Area Networks). The main purpos 9 min read
- MAN Full Form MAN stands for Metropolitan Area Network and it is made by connecting multiple LANs. MAN covers a geographical area which is known as the metropolitan area. It serves as a connection that is larger than LAN(Local Area Network) but smaller than WAN(Wide Area Network). It generally covers the area of 5 min read
- WAN Full Form A WAN (Wide Area Network) is to connect multiple smaller Local Area Networks (LANs). It is a computer network designed. WANs can help in communication, the sharing of information, and much more between systems or devices from around the world through a WAN provider. What is a WAN?WAN stands for Wide 5 min read
- Introduction of Internetworking Internetworking is combined of 2 words, inter and networking which implies an association between totally different nodes or segments. This connection area unit is established through intercessor devices akin to routers or gateway. The first term for associate degree internetwork was catenet. This i 8 min read
- Difference between Internet, Intranet and Extranet Networks are crucial in today’s globalized world because they allow the acquisition, exchange, and organization of knowledge. Of all the first order networks the Internet, Intranet, and Extranet are commonly utilized for various applications. Every network type meets specific roles that are required 5 min read
- Protocol Hierarchies in Computer Network A Protocol Hierarchy is a fixed set of rules and conventions that govern the communication between two or more computers. The hierarchical structure allows for modular design, interoperability, and ease of implementation in computer networks. What is Protocol?A protocol is simply defined as a set of 3 min read
- Network Devices (Hub, Repeater, Bridge, Switch, Router, Gateways and Brouter) Network devices are physical devices that allow hardware on a computer network to communicate and interact with each other. Network devices like hubs, repeaters, bridges, switches, routers, gateways, and brouters help manage and direct data flow in a network. They ensure efficient communication betw 10 min read
- Introduction of a Router Network devices are physical devices that allow hardware on a computer network to communicate and interact with one another. For example Repeater, Hub, Bridge, Switch, Routers, Gateway, Router, and NIC, etc. What is a Router?A Router is a networking device that forwards data packets between computer 12 min read
- Introduction of Gateways A gateway is a network connectivity device that connects two different configuration networks. Gateways are also known as protocol converters, because they play an important role in converting protocols supported by traffic on different networks. As a result, it allows smooth communication between t 5 min read
- What is a Network Switch and How Does it Work? The Switch is a network device that is used to segment the networks into different subnetworks called subnets or LAN segments. It is responsible for filtering and forwarding the packets between LAN segments based on MAC address. Switches have many ports, and when data arrives at any port, the desti 9 min read
Network Topology
- Types of Network Topology Network topology refers to the arrangement of different elements like nodes, links, or devices in a computer network. Common types of network topology include bus, star, ring, mesh, and tree topologies, each with its advantages and disadvantages. In this article, we will discuss different types of n 12 min read
- Difference between Physical and Logical Topology A Physical and Logical topologies are important concepts that govern the formation and operation of networks. In this article we will see differences between both topologies, and troubleshooting network infrastructure. What is Physical Topology?Physical topology indicates the arrangement of differen 5 min read
- What is OSI Model? - Layers of OSI Model The OSI (Open Systems Interconnection) Model is a set of rules that explains how different computer systems communicate over a network. OSI Model was developed by the International Organization for Standardization (ISO). The OSI Model consists of 7 layers and each layer has specific functions and re 14 min read
- Physical Layer in OSI Model The physical Layer is the bottom-most layer in the Open System Interconnection (OSI) Model which is a physical and electrical representation of the system. It consists of various network components such as power plugs, connectors, receivers, cable types, etc. The physical layer sends data bits from 5 min read
- Data Link Layer The data link layer is the second layer from the bottom in the OSI (Open System Interconnection) network architecture model. It is responsible for the node-to-node delivery of data. Its major role is to ensure error-free transmission of information. DLL is also responsible for encoding, decoding, an 5 min read
- Session Layer in OSI model Prerequisite : OSI Layer Introduction :The Session Layer is the 5th layer in the Open System Interconnection (OSI) model. This layer allows users on different machines to establish active communications sessions between them. It is responsible for establishing, maintaining, synchronizing, terminatin 5 min read
- Presentation Layer in OSI model Prerequisite : OSI Model Introduction : Presentation Layer is the 6th layer in the Open System Interconnection (OSI) model. This layer is also known as Translation layer, as this layer serves as a data translator for the network. The data which this layer receives from the Application Layer is extra 6 min read
- Application Layer in OSI Model The Application Layer of OSI (Open System Interconnection) model, is the top layer in this model and takes care of network communication. The application layer provides the functionality to send and receive data from users. It acts as the interface between the user and the application. The applicati 9 min read
- Protocol and Standard in Computer Networks Protocols and standards are important in computer networks. They are like the rules and guidelines that allow different devices and systems to communicate and work together smoothly. Protocols define how data is sent, received, and processed, while standards ensure that various technologies are comp 9 min read
- Examples of Data Link Layer Protocols Data Link Layer protocols are generally responsible to simply ensure and confirm that the bits and bytes that are received are identical to the bits and bytes being transferred. It is basically a set of specifications that are used for implementation of data link layer just above the physical layer 4 min read
TCP/IP Model
- TCP/IP Model The TCP/IP model is a fundamental framework for computer networking. It stands for Transmission Control Protocol/Internet Protocol, which are the core protocols of the Internet. This model defines how data is transmitted over networks, ensuring reliable communication between devices. It consists of 14 min read
- TCP/IP Ports and Its Applications A port is the logical address of any protocol; alternatively, we might think of a port as a special door for each protocol, through which all packets are routed. Another way to put it is that every protocol has a mailbox, or box, where every protocol packet is dropped. Subsequently, the recipient wi 6 min read
- What is TCP (Transmission Control Protocol)? TCP (Transmission Control Protocol) is one of the main protocols of the TCP/IP suite. It lies between the Application and Network Layers which are used in providing reliable delivery services. Transmission Control Protocol (TCP) ensures reliable and efficient data transmission over the internet. TCP 6 min read
- TCP 3-Way Handshake Process The TCP 3-Way Handshake is a fundamental process that establishes a reliable connection between two devices over a TCP/IP network. It involves three steps: SYN (Synchronize), SYN-ACK (Synchronize-Acknowledge), and ACK (Acknowledge). During the handshake, the client and server exchange initial sequen 7 min read
- Services and Segment structure in TCP The Transmission Control Protocol is the most common transport layer protocol. It works together with IP and provides a reliable transport service between processes using the network layer service provided by the IP protocol. The various services provided by the TCP to the application layer are as f 5 min read
- TCP Connection Establishment Prerequisite – TCP 3-Way Handshake Process TCP is a connection-oriented protocol and every connection-oriented protocol needs to establish a connection in order to reserve resources at both the communicating ends. Connection Establishment - TCP connection establishment involves a three-way handshake 3 min read
- TCP Connection Termination In TCP 3-way Handshake Process we studied that how connections are established between client and server in Transmission Control Protocol (TCP) using SYN bit segments. In this article, we will study how TCP close connection between Client and Server. Here we will also need to send bit segments to a 5 min read
- TCP Timers TCP uses several timers to ensure that excessive delays are not encountered during communications. Several of these timers are elegant, handling problems that are not immediately obvious at first analysis. Each of the timers used by TCP is examined in the following sections, which reveal its role in 4 min read
- Fast Recovery Technique For Loss Recovery in TCP When the RTO timer expires but an ACK is not received, the sender confirms that the packet is lost due to congestion at intermediary devices. Now sender has to tackle this congestion state carefully. Fast Recovery is the packet loss recovery technique. Recovery means becoming inactive and not transm 4 min read
- Difference Between OSI Model and TCP/IP Model Data communication is a process or act in which we can send or receive data. Understanding the fundamental structures of networking is crucial for anyone working with computer systems and communication. For data communication two models are available, the OSI (Open Systems Interconnection) Model, an 5 min read
Medium Access Control
- MAC Full Form MAC refers to Media Access Control, which is an important issue in network technology. In simple words, MAC is a series of rules through which devices can transfer data among them in a network. When a device is connected to a network, it obtains a unique MAC address. It identifies a device connected 5 min read
- Channel Allocation Problem in Computer Network Channel allocation is a process in which a single channel is divided and allotted to multiple users in order to carry user specific tasks. There are user's quantity may vary every time the process takes place. If there are N number of users and channel is divided into N equal-sized sub channels, Eac 3 min read
- Multiple Access Protocols in Computer Network Multiple Access Protocols are methods used in computer networks to control how data is transmitted when multiple devices are trying to communicate over the same network. These protocols ensure that data packets are sent and received efficiently, without collisions or interference. They help manage t 9 min read
- Carrier Sense Multiple Access (CSMA) Carrier Sense Multiple Access (CSMA) is a method used in computer networks to manage how devices share a communication channel to transfer the data between two devices. In this protocol, each device first sense the channel before sending the data. If the channel is busy, the device waits until it is 9 min read
- Collision Detection in CSMA/CD CSMA/CD (Carrier Sense Multiple Access/ Collision Detection) is a media access control method that was widely used in Early Ethernet technology/LANs when there used to be shared Bus Topology and each node ( Computers) was connected by Coaxial Cables. Nowadays Ethernet is Full Duplex and Topology is 7 min read
- Controlled Access Protocols in Computer Network Controlled Access Protocols (CAPs) in computer networks control how data packets are sent over a common communication medium. These protocols ensure that data is transmitted efficiently, without collisions, and with little interference from other data transmissions. In this article, we will discuss 6 min read
SLIDING WINDOW PROTOCOLS
- Stop and Wait ARQ Stop and Wait ARQ is a Sliding Window Protocol method used for the reliable delivery of data frames. The stop-and-wait ARQ is used for noisy channels or links to handle flow and error control between sender and receiver. The Stop and Wait ARQ protocol sends a data frame and then waits for an acknowl 9 min read
- Sliding Window Protocol | Set 3 (Selective Repeat) Prerequisite : Sliding Window Protocol - Set 1 (Sender Side), Set 2 (Receiver Side) Why Selective Repeat Protocol? The go-back-n protocol works well if errors are less, but if the line is poor it wastes a lot of bandwidth on retransmitted frames. An alternative strategy, the selective repeat protoco 3 min read
- Piggybacking in Computer Networks Pre-Requisite: Transmission Mode in Computer Networks Piggybacking is the technique of delaying outgoing acknowledgment and attaching it to the next data packet. When a data frame arrives, the receiver waits and does not send the control frame (acknowledgment) back immediately. The receiver waits u 5 min read
IP Addressing
- What is IPv4? IP stands for Internet Protocol version v4 stands for Version Four (IPv4), is the most widely used system for identifying devices on a network. It uses a set of four numbers, separated by periods (like 192.168.0.1), to give each device a unique address. This address helps data find its way from one 4 min read
- What is IPv6? The most common version of the Internet Protocol currently is IPv6. The well-known IPv6 protocol is being used and deployed more often, especially in mobile phone markets. IP address determines who and where you are in the network of billions of digital devices that are connected to the Internet. It 5 min read
- Introduction of Classful IP Addressing An IP address is an address that has information about how to reach a specific host, especially outside the LAN. An IP address is a 32-bit unique address having an address space of 232. Classful IP addressing is a way of organizing and managing IP addresses, which are used to identify devices on a n 10 min read
- Classless Addressing in IP Addressing The Network address identifies a network on the internet. Using this, we can find a range of addresses in the network and total possible number of hosts in the network. Mask is a 32-bit binary number that gives the network address in the address block when AND operation is bitwise applied on the mas 7 min read
- Classful vs Classless Addressing Classful and Classless addressing are methods used in networking to manage IP addresses. Classful addressing divides IP addresses into fixed classes (A, B, C, D, E), each with predefined ranges. In contrast, classless addressing, also known as CIDR (Classless Inter-Domain Routing), offers more flexi 7 min read
- Classless Inter Domain Routing (CIDR) Classless Inter-Domain Routing (CIDR) is a method of IP address allocation and IP routing that allows for more efficient use of IP addresses. CIDR is based on the idea that IP addresses can be allocated and routed based on their network prefix rather than their class, which was the traditional way o 6 min read
- Supernetting in Network Layer Supernetting is the opposite of Subnetting. In subnetting, a single big network is divided into multiple smaller subnetworks. In Supernetting, multiple networks are combined into a bigger network termed a Supernetwork or Supernet. In this article, we'll explore the purpose and advantages of supernet 4 min read
- Introduction To Subnetting Subnetting is the process of dividing a large network into smaller networks called as "subnets." Subnets provides each group of devices have thier own space to communicate, that ultimately helps network to work easily. This also boosts security and makes it easier to manage the network, as each subn 8 min read
- Difference between Subnetting and Supernetting Subnetting is the procedure to divide the network into sub-networks or small networks, these smaller networks are known as subnets. The subnet is also defined as an internal address made up of a combination of a small network and host segments. In a subnet, a few bits from the host portion are used 4 min read
- Types of Routing Routing is the process of determining paths through a network for sending data packets. It ensures that data moves effectively from source to destination, making the best use of network resources and ensuring consistent communication. Routing performed by layer 3 (or network layer) devices to delive 6 min read
- Difference between Static and Dynamic Routing Routing is a vital communication mechanism that governs how data packets travel from source to destination. Effective routing ensures that data is transferred across networks in an efficient, reliable, and timely manner. There are two main forms of routing: static and dynamic. In this article, we wi 4 min read
- Unicast Routing - Link State Routing Prerequisite: Distance Vector Routing, Dijkstra algorithm Unicast means the transmission from a single sender to a single receiver. It is a point-to-point communication between the sender and receiver. There are various unicast protocols such as TCP, HTTP, etc. TCP is the most commonly used unicas 7 min read
- Distance Vector Routing (DVR) Protocol Distance Vector Routing (DVR) Protocol is a method used by routers to find the best path for data to travel across a network. Each router keeps a table that shows the shortest distance to every other router, based on the number of hops (or steps) needed to reach them. Routers share this information 5 min read
- Fixed and Flooding Routing algorithms In most situations, packets require multiple hops to make a journey towards the destination. Routing is one of the most complex and crucial aspects of packet-switched network design. Desirable Properties of Routing Algorithms:- Correctness and SimplicityRobustness: Ability of the network to deliver 5 min read
- Introduction of Firewall in Computer Network In the world of computer networks, a firewall acts like a security guard. Its job is to watch over the flow of information between your computer or network and the internet. It's designed to block unauthorized access while allowing safe data to pass through. Essentially, a firewall helps keep your d 12 min read
Congestion Control Algorithms
- Congestion Control in Computer Networks Congestion control is a crucial concept in computer networks. It refers to the methods used to prevent network overload and ensure smooth data flow. When too much data is sent through the network at once, it can cause delays and data loss. Congestion control techniques help manage the traffic, so al 8 min read
- Congestion Control techniques in Computer Networks Congestion control refers to the techniques used to control or prevent congestion. Congestion control techniques can be broadly classified into two categories: Open Loop Congestion ControlOpen loop congestion control policies are applied to prevent congestion before it happens. The congestion contro 5 min read
- Computer Network | Leaky bucket algorithm In the network layer, before the network can make Quality of service guarantees, it must know what traffic is being guaranteed. One of the main causes of congestion is that traffic is often bursty. To understand this concept first we have to know little about traffic shaping. Traffic Shaping is a m 11 min read
- TCP Congestion Control TCP congestion control is a method used by the TCP protocol to manage data flow over a network and prevent congestion. TCP uses a congestion window and congestion policy that avoids congestion. Previously, we assumed that only the receiver could dictate the sender’s window size. We ignored another e 4 min read
Network Switching
- Circuit Switching in Computer Network Circuit Switching is a type of switching, in which a connection is established between the source and destination before communication. This connection receives the complete bandwidth of the network until the data is transferred completely. However, circuit switching can be inefficient and costly du 9 min read
- Message switching techniques Switching is the technique by which nodes control or switch data to transmit it between specific points on a network. In message switching the entire message is transmitted without any break from one node to another. There is no direct link present between the sender and the receiver in message swit 4 min read
- Packet Switching and Delays in Computer Network Packet Switching in computer networks is a method of transferring data to a network in the form of packets. In order to transfer the file fast and efficiently over the network and minimize the transmission latency, the data is broken into small pieces of variable length, called Packet. At the destin 7 min read
- Differences Between Virtual Circuits and Datagram Networks Computer networks that provide connection-oriented services are called Virtual Circuits while those providing connection-less services are called Datagram networks. For prior knowledge, the Internet that we use is based on a Datagram network (connection-less) at the network level as all packets from 7 min read
Application Layer:DNS
- Domain Name System (DNS) in Application Layer The Domain Name System (DNS) is like the internet's phone book. It helps you find websites by translating easy-to-remember names (like www.example.com) into the numerical IP addresses (like 192.0.2.1) that computers use to locate each other on the internet. Without DNS, you would have to remember lo 10 min read
- Details on DNS DNS (Domain Name System) allows you to interact with devices on the Internet without having to remember long strings of numbers. Each computer on the Internet has its own unique address, known as an IP address, just like every home has a unique address for sending direct mail. 104.26.10.228 is an IP 5 min read
- Introduction to Electronic Mail Introduction:Electronic mail, commonly known as email, is a method of exchanging messages over the internet. Here are the basics of email:An email address: This is a unique identifier for each user, typically in the format of [email protected] email client: This is a software program used to send, 4 min read
- E-Mail Format Electronic Mail (e-mail) is one of the most widely used services of the Internet. This service allows an Internet user to send a message in a formatted manner (mail) to other Internet users in any part of the world. Message in the mail not only contain text, but it also contains images, audio and vi 3 min read
- World Wide Web (WWW) The World Wide Web (WWW), often called the Web, is a system of interconnected webpages and information that you can access using the Internet. It was created to help people share and find information easily, using links that connect different pages together. The Web allows us to browse websites, wat 6 min read
- HTTP Full Form HTTP stands for HyperText Transfer Protocol. It is the main way web browsers and servers communicate to share information on the internet. Tim Berner invents it. HyperText is the type of text that is specially coded with the help of some standard coding language called HyperText Markup Language (HTM 9 min read
- Streaming Stored Video Streaming of videos involve, storing of prerecorded videos on servers. Users send request to those servers.Users may watch the video from the start till the end, and may pause it anytime, do a forward or reverse skip, or stop the video whenever they want to do so. There are 3 video streaming categor 5 min read
- What is a Content Distribution Network and how does it work? Over the last few years, there has been a huge increase in the number of Internet users. YouTube alone has 2 Billion users worldwide, while Netflix has over 160 million users. Streaming content to such a wide demographic of users is no easy task. One can think that a straightforward approach to this 4 min read
CN Interview Quetions
- Top 50 Plus Networking Interview Questions and Answers for 2024 Networking is defined as connected devices that may exchange data or information and share resources. A computer network connects computers to exchange data via a communication media. Computer networking is the most often asked question at leading organizations such Cisco, Accenture, Uber, Airbnb, G 15+ min read
- Top 50 TCP/IP Interview Questions and Answers 2024 Understanding TCP/IP is essential for anyone working in IT or networking. It's a fundamental part of how the internet and most networks operate. Whether you're just starting or you're looking to move up in your career, knowing TCP/IP inside and out can really give you an edge. In this interview prep 15+ min read
- Top 50 IP Addressing Interview Questions and Answers In today’s digital age, every device connected to the internet relies on a unique identifier called an IP Address. If you’re aiming for a career in IT or networking, mastering the concept of IP addresses is crucial. In this engaging blog post, we’ll explore the most commonly asked IP address intervi 15+ min read
- Last Minute Notes - Computer Networks See Last Minute Notes on all subjects here. OSI Model Physical Layer Data Link layer Network Layer Transport Layer Presentation & Session layer Application Layer OSI ModelOSI stands for Open Systems Interconnection. It has been developed by ISO– International Organization for Standardization, in 11 min read
- Computer Network - Cheat Sheet A computer network is an interconnected computing device that can exchange data and share resources. These connected devices use a set of rules called communication protocols to transfer information over physical or wireless technology. Modern networks offer more than just connectivity. Enterprises 15+ min read
- Network Layer [mtouchquiz 103] 1 min read
- Transport Layer [mtouchquiz 104] 1 min read
- Application Layer [mtouchquiz 106] 1 min read
Improve your Coding Skills with Practice
What kind of Experience do you want to share?
- Why Neos Networks?
- Our leaders
- Product finder tool
- Cloud Connect
- Dedicated Internet Access
- Optical Wavelengths
- Financial services
- Systems integrators
- Energy and utilities
- Transport and logistics
- Public Sector
- Critical National Infrastructure (CNI)
- Become a partner
- Our network
- Interactive network map
- Network map PDF
- Plant enquiries
- Customer stories
- Press releases
- Product brochures
- Business General
What is the OSI model?
Discover how the model structures network communications into seven layers, how they work, and why it matters for networking..
The 7 layers of the OSI model
How does the osi model work, osi model vs tcp/ip model, why is the osi model important, osi model disadvantages, making connectivity work, get ultrafast, low latency optical wavelengths.
The Open Systems Interconnection (OSI) model describes how computer systems communicate across networks. Published by the International Organization for Standardization (ISO) in 1984, it divides communications into seven layers, providing a common basis for developing networking standards.
It’s a reference model, a conceptual framework that outlines the structure and relationship between a network’s components without prescribing specific implementation methods. It provides a universal language for network operators, developers, and students to understand, design and implement complex networks.
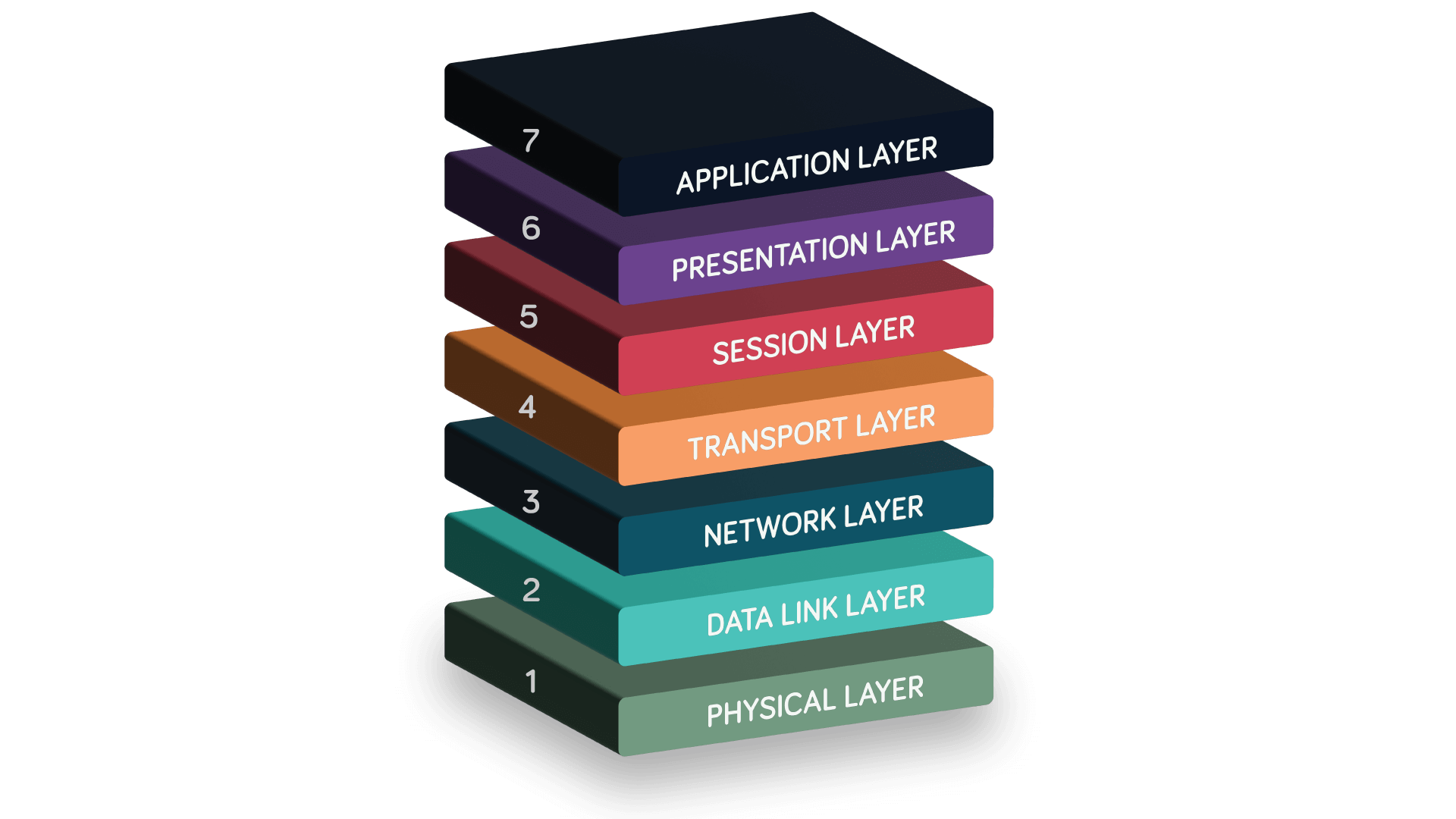
The OSI model organises network communications into a stack of seven layers:
- The Physical Layer
- The Data Link Layer
- The Network Layer
- The Transport Layer
- The Session Layer
- The Presentation Layer
- The Application Layer
Each layer performs a specific function and interacts with the layers above and below, ensuring efficient data transmission. Typically, the layers are listed from top to bottom (7 to 1) to reflect the data flow during communication, starting from the user’s application at the Application Layer and moving down to the Physical Layer.
7 layers of the OSI model
Here’s a breakdown of the seven layers and their roles in a network.
7 layers explained
When data is transmitted over a network, it moves sequentially through the seven layers, from the Application Layer at the top to the Physical Layer at the bottom.
For example, here’s what happens when you send an email:
- You write a message in an email app like Gmail or Outlook and click “send”. The email client uses a protocol like SMTP to process your message ( Application Layer ).
- The email client formats your message for transmission, including encryption if enabled ( Presentation Layer ).
- A session is established between your device and the email server to manage the ongoing data exchange ( Session Layer ).
- The email data is divided into smaller segments for transmission, and protocols like TCP and UDP ensure they’re delivered reliably ( Transport Layer ).
- The email segments are assigned source and destination IP addresses to be routed across the network ( Network Layer ).
- The IP packets are encapsulated into frames to be transmitted over the local network ( Data Link Layer ).
- The frames are converted into electrical, optical, or wireless signals and transmitted through a physical medium like a network cable or Wi-Fi ( Physical Layer ).
At the receiving end, the process is reversed: the data travels up from the Physical Layer to the Application Layer, reconstructing the email for its recipient.
Another significant networking framework is the Transmission Control Protocol/Internet Protocol model (TCP/IP) , also known as the Internet Protocol Suite. Unlike the OSI model, which is primarily theoretical, TCP/IP is a practical framework designed specifically for implementing internet communications.
Initially developed for the US military’s ARPANET , the forerunner of the internet, the TCP/IP model consists of just four layers:
- The Application Layer combines the functions of OSI’s Application, Presentation and Session layers, managing high-level protocols and user interactions.
- The Transport Layer uses protocols like TCP and UDP to ensure data transfer between end systems, like OSI’s Transport Layer.
- The Internet Layer manages addressing and routing using the Internet Protocol, like OSI’s Network Layer.
- The Link Layer handles data transmission over physical media, like cables and Wi-Fi, combining the functions of OSI’s Physical and Data Link layers.
OSI model vs TCP/IP model: comparing layers
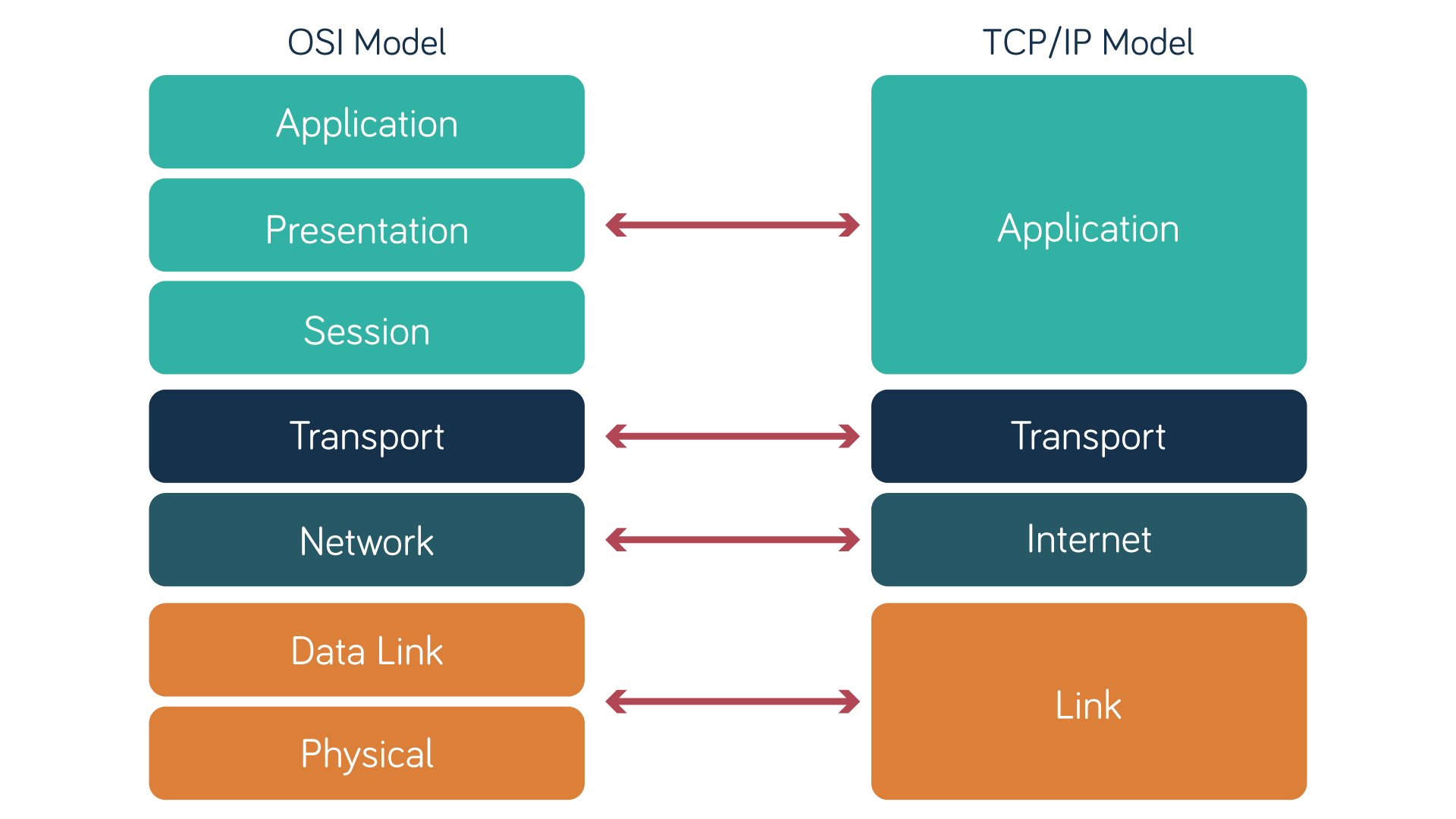
Here’s a summary of the main differences between the two:
In short, the OSI model is a comprehensive theoretical framework that standardises network communications without relying on specific protocols. In contrast, TCP/IP is a simpler, practical model that defines and supports the implementation of internet protocols.
While the TCP/IP model is more widely used in practice because it underpins the internet, the OSI model remains significant.
Although theoretical, the OSI model provides a detailed understanding of fundamental network architecture, making it valuable for several reasons:
- Standardisation and interoperability : The model provides a universal framework, promoting the development of interoperable protocols and devices.
- Troubleshooting and security : The multi-layered structure allows administrators to identify and fix technical or security failures in their specific layers without disrupting the others.
- Education and design : It’s a foundational model for IT professionals and students to share knowledge about network architecture and adapt networks for the future.
Despite its value, the OSI model has its limitations. First, real-world networking technologies don’t always fit neatly into its framework, and the functions of its layers can sometimes overlap in practice.
In addition, its comprehensive nature can make it overly complex for practical use. The simpler, more practical TCP/IP model has largely supplanted the OSI model, especially for internet communications.
However, the OSI model remains a fundamental theoretical framework. Whether you're a network professional, student, or tech enthusiast, it provides valuable insight into the complex world of computer networking.
At Neos Networks, we use the OSI model to visualise complex networks and make connectivity work for businesses across the UK.
For example, optical wavelengths operate in the Physical Layer (layer 1), enabling high-bandwidth data transmission across fibre optic networks. In contrast, Ethernet primarily functions at the Data Link Layer (layer 2) but also defines standards for some layer 1 components, like cables and connectors.
If you’re looking to supercharge your business with high capacity connectivity for the future, get in touch . We’ll be happy to make connectivity work for you.
RELATED PRODUCTS
Our Optical connectivity services deliver low latency, high capacity networking solutions across the UK.
We deliver high capacity, low latency business Ethernet services across the UK with capacities ranging from 10Mbps to 10Gbps.
OSI model FAQs
The OSI model is a guide for designing, implementing, and troubleshooting network protocols and architectures. Although the TCP/IP model is more widely used in practice due to its crucial role in the internet, the OSI model helps us visualise and understand complex networking processes.
Protocols establish the rules and standards for communication within each layer of the OSI model. But the model isn’t tied to any specific protocol. Each layer can use various protocols, which can evolve independently without disrupting the model’s overall structure.
Encapsulation is the process of adding extra information (headers and trailers) to data as it moves from layer to layer of the OSI model. This ensures that each layer can correctly interpret and transmit the data across the network. At the receiving end, this is reversed: each layer removes its header or trailer as the data moves to the top Application Layer – a process called decapsulation.
No, each layer only communicates with the layers directly above and below it. This structure ensures data is processed systematically and flows efficiently from the source to the destination.
Get high-bandwidth business Ethernet
You might also like.

What is a network-to-network interface (NNI)?
- 27 February 2024

What is data centre interconnect (DCI)?
- 1 August 2024

What are Optical Wavelengths?
- 20 March 2024
We can connect you anywhere in the UK
Discover our network reach
Great news!
" [poscode] " can be reached with our expanded network
Speak to a representatitive to discuss your options
Learn about our prices using our online tool, LIVEQUOTE
" [poscode] " can not be reached with our expanded network
[postcode] can be reached with our expanded network
Your details
Exploring the 3 layers of software interactions (APIs)
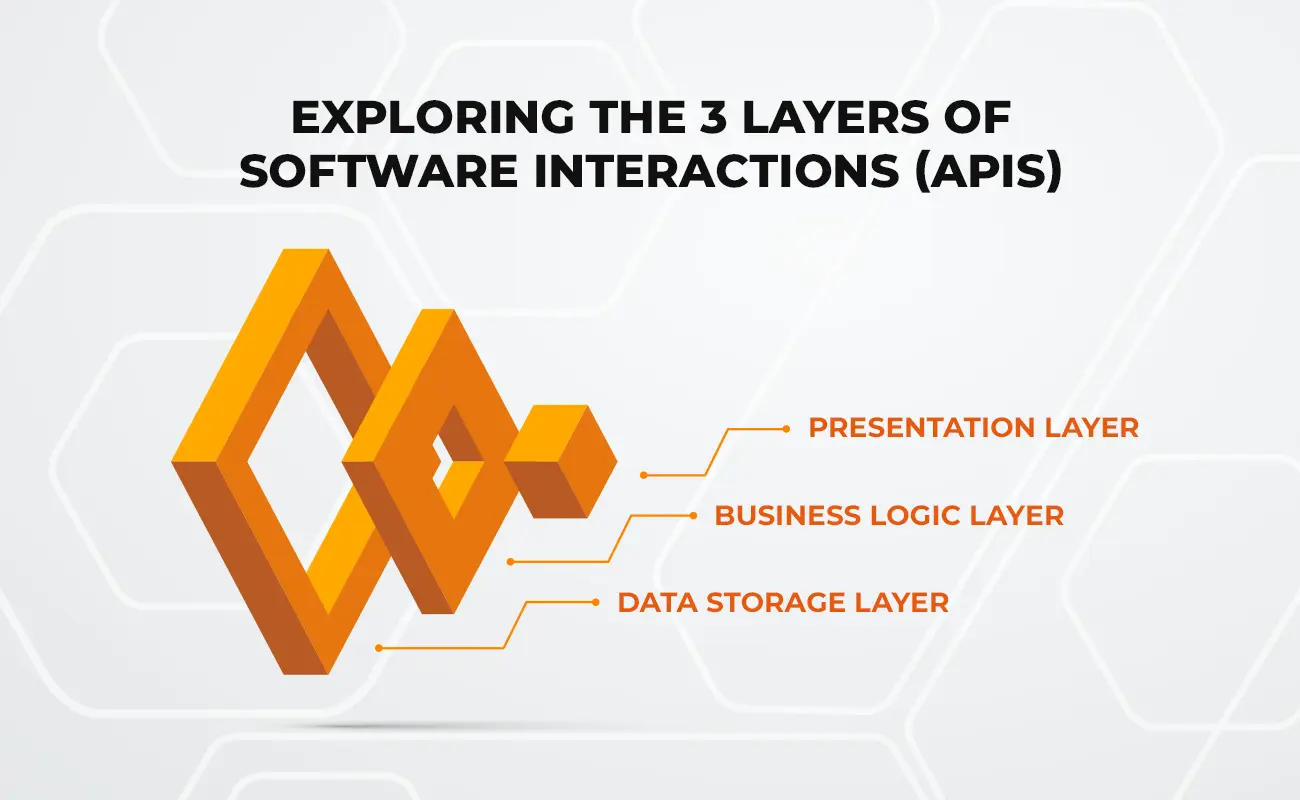
Application Programming Interfaces, commonly known as APIs, are a set of protocols, routines, and tools that enable software applications to interact with each other. They allow different software applications to exchange information seamlessly and efficiently.
APIs have become increasingly important in today's digital world, as they enable developers to build powerful applications that can connect with other services and platforms. APIs can be broken down into three different layers, each of which serves a different purpose.
In this blog post, we will explore the three layers of APIs and what they do.
1. Presentation Layer
The presentation layer, also known as the "API endpoint," is the layer that developers interact with most frequently. This layer provides a user-friendly interface for developers to access the functionality and data of the underlying service. It is responsible for processing incoming requests and returning responses in a format that developers can easily understand.
The presentation layer can take many different forms, depending on the requirements of the API. It could be a REST API that uses HTTP requests to exchange data or a SOAP API that uses XML messages to communicate. Regardless of the specific implementation, the presentation layer is the public-facing aspect of the API and is the first point of contact for developers.
2. Business Logic Layer
The business logic layer, also known as the "API middleware," is the layer that contains the core logic of the API. It is responsible for processing the requests received from the presentation layer and generating responses based on the requested actions.
The business logic layer is where the API's core functionality resides. It may perform data validation, authentication and authorization, database queries, or other complex operations. This layer is typically developed by the service provider and is not exposed directly to developers.
3. Data Storage Layer
The data storage layer, also known as the "API database," is the layer where all of the data used by the API is stored. This layer is responsible for managing data storage, retrieval, and modification. It may use a variety of database technologies such as SQL, NoSQL, or object-oriented databases.
The data storage layer is the most critical component of the API since it holds the data that the API relies on. If the data storage layer fails, the entire API may fail. Therefore, it is crucial to ensure that the data storage layer is designed and implemented correctly.
In conclusion, APIs consist of three layers: presentation layer, business logic layer, and data storage layer. Each layer plays a crucial role in the API's functionality and performance. Understanding the three layers of an API is essential for developers looking to build robust, reliable, and scalable APIs.
Related articles
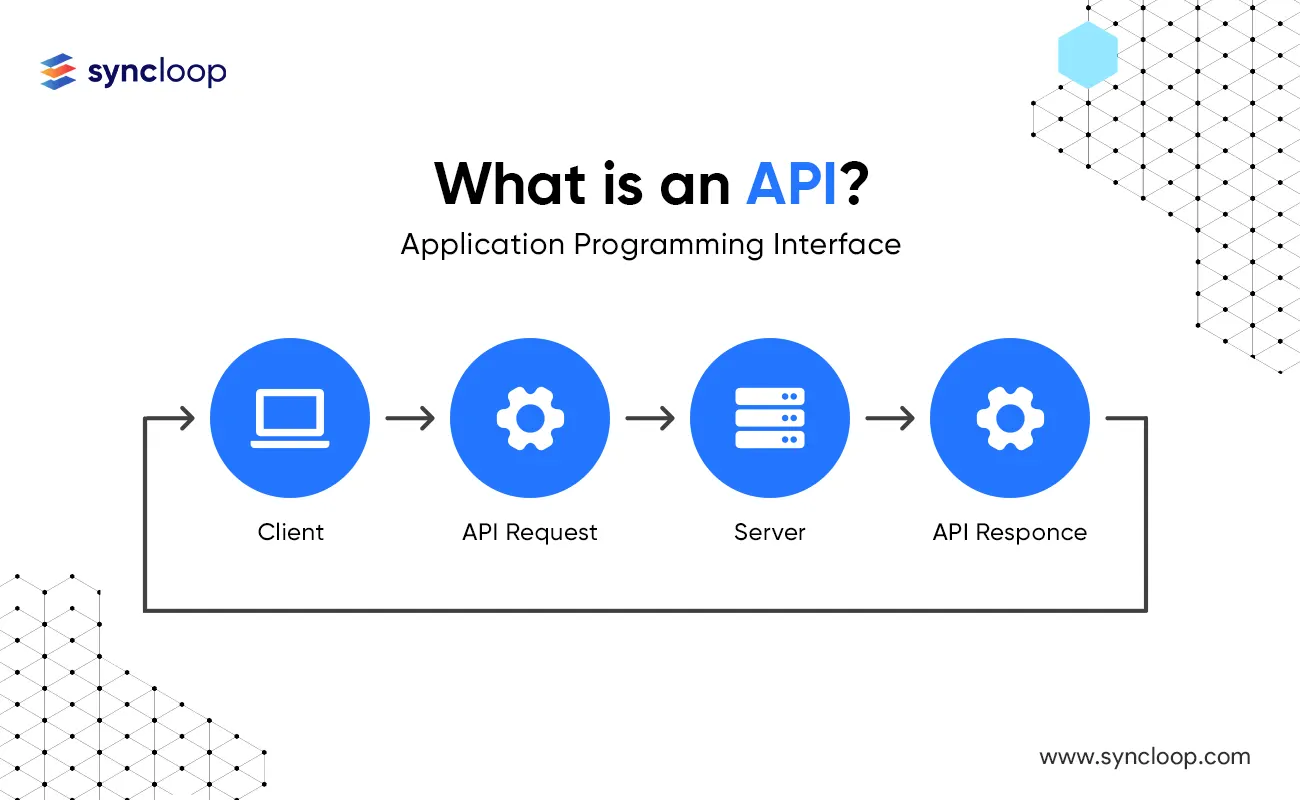
What is Application Programming Interface (API)?
An API is a set of rules and practices that allow two applications to communicate. This means that one can use one application to retrieve data from another application or send data to another application.

IMAGES
COMMENTS
The presentation tier and the data tier cannot communicate directly with one another. Tier versus layer. In discussions of three-tier architecture, layer is often used interchangeably – and mistakenly – for tier, as in 'presentation layer' or 'business logic layer'. They aren't the same.
Aug 26, 2015 · I've mentioned three layers here, but it's common to see architectures with more than three layers. A common variation is to put a service layer between the domain and presentation, or to split the presentation layer into separate layers with something like Presentation Model. I don't find that more layers breaks the essential pattern, since ...
This layer focuses on data representation and ensures that data is presented in a consistent and meaningful way. One of the key functions of the Presentation Layer is data encryption and decryption, which helps secure data transmission over the network. Another important aspect of the Presentation Layer is data compression.
Nov 27, 2013 · The presentation layer should only be concerned about presenting data, not about how to retrieve it. Suppose you move your whole database into CSV files (I know, crazy idea), then your presentation layer should not be aware of this at all. So ideally, you have a business layer method that returns just the data you want to show to the user.
2 days ago · Layer 6: The Presentation Layer. The Presentation Layer focuses on data format and encryption. It ensures that data sent by one device can be read by another, regardless of format differences. Responsibilities: Translates data between different formats. Encrypts and decrypts data for secure transmission.
Aug 2, 2022 · Data from Application Layer <=> Presentation layer <=> Data from Session Layer. The presentation layer, being the 6th layer in the OSI model, performs several types of functions, which are described below-Presentation layer format and encrypts data to be sent across the network.
Sublayers of presentation layer in the OSI model: The presentation layer in the OSI model is classified into two sublayers: Common Application Service Element (CASE): This sublayer offers services to layer-7, i.e., the application layer, and requests services from layer-5, i.e., the session layer. It supports various application services, such ...
Oct 21, 2024 · The presentation layer translates data from the application layer for transmission to the application layer for use by the intended device. It makes the data readable to and from the application layer. This layer is where encryption occurs when data is sent from the application layer, and when decryptions occur, it is sent back to the ...
The Internet Layer manages addressing and routing using the Internet Protocol, like OSI’s Network Layer. The Link Layer handles data transmission over physical media, like cables and Wi-Fi, combining the functions of OSI’s Physical and Data Link layers. OSI model vs TCP/IP model: comparing layers
May 19, 2024 · The data storage layer is the most critical component of the API since it holds the data that the API relies on. If the data storage layer fails, the entire API may fail. Therefore, it is crucial to ensure that the data storage layer is designed and implemented correctly. In conclusion, APIs consist of three layers: presentation layer, business ...