Due: Mon Jun 28 11:59 pm No late submissions accepted.
Assignment by Michael Chang, Julie Zelenski, and Chris Gregg, with modifications by Nick Troccoli
No late submissions are accepted on this assignment . The deadline is firm without exception.

Learning Goals
The goals for this assignment are for you to get familiar with working in the Unix environment, and editing/building/running C programs.
Unix and C Resources
The pages in the Handouts dropdown above have information, including videos, for various Unix commands, tools, and more that we'll be using this quarter. We highly recommend reading through the getting started guide and unix guide and trying out various commands and tools yourself, to get practice. In particular, some of the activities in this assignment will rely on information you will need to read up on there. Note that you don't need to memorize all the information, but you may start to memorize lots of commands just by repetition.
Before starting the assignment, double-check that you are comfortable with these Unix fundamentals - discussed in the getting started guide.
View Getting Started Guide
- Log in to Myth
- Did you create a CS107 directory to hold and organize your work?
- Can you find the code being demoed in lecture?
- You should be able to create a new file, edit its contents, save, and exit.
- You should be able to interact with Emacs via the mouse (e.g. selecting text, scrolling, etc.)
- If you encounter a command that is new to you, how can you get more information about it?
- Have you tried using tab-completion to avoid manually typing long commands/paths?
Additionally, take a look at the guide in the assignments dropdown about working on assignments. It outlines everything you need to know about working through a CS107 assignment, from getting the starter code to testing to submitting. We will refer to this document many times throughout this assignment, so keep it handy as you work through this page.
View Assignments Guide
Cloning The Assignment
To get started on the assignment, you must "clone" the starter code to get a copy you can work on. Check out the assignments guide for how to do this.
If you attempt to clone and receive an error that the repository does not exist :
- double-check for typos in the path. The path needs to be typed exactly as specified. This includes the odd-looking $USER at end, which is a environment variable that expands into your username automatically.
- be sure you are logged into myth
If you confirm you are on a Myth system and your correctly-typed path is not available, this indicates that you were not on the Axess enrollment list at the time we created the student starter code projects. Please send an email to the course staff and tell us your username so we can manually set up the starter code for you. Please make sure to enroll in Axess as soon as possible so that the starter code is automatically generated for you in the future.
Provided Files
The starter project contains the following:
- readme.txt : a text file where you will answer questions for the assignment
- triangle.c , Makefile and custom_tests : used to build and test the triangle program
- SANITY.ini : the configuration for Sanity Check. You can ignore this file.
- server_files : a folder that pertains to the first part of the assignment.
- triangle_soln : an executable solution for the Triangle program. You can run this program to see how a completed solution program should behave. This program is also used to check correctness in sanity check.
- tools : contains symbolic links to the sanitycheck and submit programs for testing and submitting your work.
Symbolic links mean that the files actually live in the CS107 class directory, but appear just like normal files in your starter code folder. Note that the shared directories are not editable by you, so you will not be able to create, edit, or delete files within these directories, since they actually live in the CS107 class directory.
1. Enrollment Confirmation
In order to complete your enrollment in CS107, you must fill out the readme with some information about you and accept the course Honor Code policy.
Open the readme.txt file in your editor now and edit as appropriate.
As part of this, you must complete the Honor Code Form. When grading your assign0, we will check that you made a submission through this form, so please make sure to fill it out!
Access the Honor Code Form
Course TODOs:
Once you have done this, also complete the following setup tasks:
- Join our course discussion forum by visiting the Getting Help page.
- Remember to submit your lab preferences (not first-come-first-serve) between Tue Jun 22 5:00 pm PDT and Sun Jun 27 5:00 pm PDT .
2. Intruder Detection
For this activity, you will investigate a simulated break-in and answer the questions below. Type your answers into the readme.txt file. For each, briefly describe (in 1-2 sentences) how you arrived at that answer and what Unix commands you used (Emacs text editor keyboard shortcuts do not classify as Unix commands).
Activity Learning Goals: In class we have taught you the basics of Unix: how to login to myth, how to make directories, and how to list files. In this activity, you will further develop your Unix skills by understanding how to use common Unix commands beyond what we know so far. The how-to's of many of the commands you will learn are available on our CS107 Unix guide, under "Handouts". We recommend you browse this guide as you complete this activity:
View Unix Guide
Situation: An intruder had broken into your dorm's unix-based server and deleted most of the files! Fortunately, there is a backup of the server contents, but before restoring the files, you'd like to know who the intruder was and what they did. With your newly-developed Unix skills, you are just the expert to help investigate.
The key files are available in the directory samples/server_files , which you can access within your assign0 directory.
The first thing you want to determine is the username of the intruder. The server is used by many different users. Each user has a home directory under home/ . For example, the home directory for the user bob would be the path home/bob . The file users.list contains a list of all the authorized users. In an uncompromised system, each home directory would correspond to a user on the authorized list and vice versa. The intruder is not an authorized user and they gained illicit access by inserting their own home directory onto the system. This means there is one home directory that doesn't belong, and your job is to find it.
Manually cross-comparing the users.list to the directory contents would be time-consuming. Instead, what Unix commands can you use to help? Check out the Unix guide for some ideas.
Hint: the samples/ folder and everything inside it is a shared, read-only folder for all students for this assignment. For this reason, you can't create any new files within samples , and you can't create new files outside of samples from within the samples folder. If you need to create a temporary file, try creating it directly inside your assign0 directory instead.
- What is the username of the intruder? Include the details on how you figured out the answer, and what Unix command(s) you used. You should use Unix commands as much as possible, even if other by-hand alternatives exist (as a clarification, commands within the Emacs text editor are not Unix commands).
Now that you know the intruder's username, you can examine the files in intruder's home directory to learn what they were up to. Though the intruder tried to delete all the home directory files as part of covering their tracks, you can see that this supposedly empty directory is still taking up space. Perhaps something interesting was overlooked?
Take a closer look to find out what files have been left behind. Open each of the files in the intruder's home directory to see their contents.
- There is one file in the intruder's home directory that provides critical information about their activities. What file is that and what does it contain? Include the details on how you figured out the answer, and what Unix command(s) you used. You should use Unix commands as much as possible, even if other by-hand alternatives exist (as a clarification, commands within the Emacs text editor are not Unix commands).
You believe that the intruder used sudo to execute some commands as a privileged user. You want to identify those commands, but the file is rather long to comb through by hand. What Unix command can you use to extract the information you seek?
- Which commands did the intruder execute using sudo ? Include the details on how you figured out the answer, and what Unix command(s) you used. You should use Unix commands as much as possible, even if other by-hand alternatives exist (as a clarification, commands within the Emacs text editor are not Unix commands).
3. C Introduction
The final task of the assignment gives you practice using the Unix development tools to edit, build, run, and test a short C program.
In your assign0 folder, type make . This will build the program named triangle . Run the program to see what it does:
You should be rewarded with an ascii representation of Sierpinski's triangle - cool! Try to run make again:
This isn't an error; it simply means that nothing has changed in the program's source, so there isn't anything to re-compile.
Open triangle.c in a text editor and change the value of the variable nlevels in main from 3 to 5. After you have saved the file, you must then use make to re-build the program , and then you can run the newly built program to see the bigger triangle. If you forget to re-run make , you will run the original version of the program that has not been updated!
The starter code uses a fixed constant for the number of levels to print. Your task is to extend the program to take an optional command-line argument that allows the user to dictate the number of levels. With no arguments, ./triangle should default to a level 3 triangle, but the user should also be able to provide a numeric argument, e.g. ./triangle 4 or ./triangle 2 , to control the number of levels. If given an unworkable number of levels (anything larger than 8 gets unwieldy and negative would be nonsensical), your program should reject it with a helpful and explanatory message that informs the user how to correct their error, and then terminate early with an exit status of 1 (this indicates something went wrong with the program execution). The best function to do this is the error function; check out the manual pages ( man 3 error ) for more information about this function (Fun fact: man pages have information for both Unix commands and built-in C functions!) One note is that you should specify an errnum of 0 , since we don't need to print out an error message corresponding to a specific error code. Try to figure out the values for the remaining parameters. You must exactly match the error message of the sample solution . Note : You may assume that the user will enter an integer value, and do not have to worry about handling arguments that are not valid integers. If the user specifies multiple command-line arguments, you should use just the first one .
When applicable, you should define constants in your program rather than using "magic numbers", which are numbers hardcoded into your program. See the starter code for an example of how to do this in C.
In order to complete this task, the program will need to convert the user's argument (supplied in string form) into an integer. The C library function atoi can be used to do this. Review the man page ( man atoi ) or look in your C reference to get acquainted with this function.
Now let's test the program implementation. The Sanity Check tool is included in the assignment starter project, and acts as a testing aid. Read the guide to working on assignments for more information about how to use it.
The default sanitycheck for assign0 has one test that validates the output of the triangle program when given no argument. The unmodified starter program code should pass this test. After you have extended the triangle program to accept an argument, the program should continue to pass the default sanitycheck, but you will need new tests to validate the argument-handling.
You extend sanitycheck to test additional cases by using a custom tests file. The starter project includes a custom_tests file. Open this file in your editor to see the format. Now consider what additional test cases are needed to fully vet the output of your new, improved triangle program. You will need at least two additional tests. Add those tests to this custom_tests file and use these with sanitycheck to validate that your triangle program passes all tests. For more information about how to run your custom tests, check out the guide to working on assignments. For tips on thorough testing, check out our testing guide, linked to from the assignments dropdown.
Once you are finished working and have saved all your changes, check out the guide to working on assignments for how to submit your work. We recommend you do a trial submit in advance of the deadline to familiarize yourself with the process and allow time to work through any snags. You may submit as many times as you would like; we will grade the latest submission.
You should only need to modify the following files for this assignment: readme.txt , triangle.c , custom_tests .
We would also appreciate if you filled out this homework survey to tell us what you think once you submit. We appreciate your feedback!
The assignment is graded out of about 25 points. Full credit will be awarded for reasonable answers to the questions in the readme.txt file and a correct modification of triangle.c and custom_tests . This assignment is worth many fewer points than other assignments, but we expect everyone will earn all points; go team!
Post-Assignment Check-in
How did the assignment go for you? We encourage you to take a moment to reflect on how far you've come and what new knowledge and skills you have to take forward. Once you finish this assignment, you should have your environment configured and should be starting to feel comfortable with the command-line interface, navigating the filesystem, using Emacs, and getting around Unix. You're off to a great start!
To help you gauge your progress, for each assignment/lab, we identify some of its takeaways and offer a few thought questions you can use as a self-check on your post-task understanding. If you find the responses don't come easily, it may be a sign a little extra review is warranted. These questions are not to be handed in or graded. You're encouraged to freely discuss these with your peers and course staff to solidify any gaps in you understanding before moving on from a task. They could also be useful as review for assessments.
- Identify a few different techniques to avoid painstakingly re-typing a long Unix command to execute.
- How do you copy and paste in Emacs?
- Explain the purpose and use of the CS107 tools sanitycheck and submit . How do you customize the tests used by sanity check?
Frequently Asked Questions
When i try to run the triangle program in my directory, it responds "command not found". what's wrong.
Unix wants you to instead refer to the program by its full name ./triangle . See our Unix guide for more information.
How do I use the sample executable? How does it relate to sanity check?
Our provided sample executable can be used a reference implementation during testing. Run the solution and your program on the same input and verify the output is the same:
If your program produces the same result as the sample, all is good. You can manually "eyeball" the two results, or run sanitycheck with the provided tests, or your own tests. You can find more information about sanity check in our guide to working on assignments.
- Engineering Mathematics
- Discrete Mathematics
- Operating System
- Computer Networks
- Digital Logic and Design
- C Programming
- Data Structures
- Theory of Computation
- Compiler Design
- Computer Org and Architecture
Introduction to UNIX System
UNIX is an innovative or groundbreaking operating system which was developed in the 1970s by Ken Thompson, Dennis Ritchie, and many others at AT&T Laboratories. It is like a backbone for many modern operating systems like Ubuntu, Solaris, Kali Linux, Arch Linux, and also POSIX. Originally, It was designed for developers only, UNIX played a most important role in the development and creation of the software and computing environments. Its distribution to government and academic institutions led to its widespread adoption across various types of hardware components. The core part of the UNIX system lies in its base Kernel, which is integral to its architecture, structure, and key functionality making it the heart of the operating system.
For those preparing for exams like GATE , a thorough understanding of operating systems, including Unix, is essential. Our GATE course provides an in-depth exploration of Unix, covering its history, structure, and key concepts that are crucial for the exam
The basic design philosophy of UNIX is to provide simple, powerful tools that can be combined to perform complex tasks. It features a command-line interface that allows users to interact with the system through a series of commands, rather than through a graphical user interface (GUI).
Some of the Key Features of UNIX Include
- Multiuser support: UNIX allows multiple users to simultaneously access the same system and share resources.
- Multitasking: UNIX is capable of running multiple processes at the same time.
- Shell scripting: UNIX provides a powerful scripting language that allows users to automate tasks.
- Security: UNIX has a robust security model that includes file permissions, user accounts, and network security features.
- Portability: UNIX can run on a wide variety of hardware platforms, from small embedded systems to large mainframe computers.
- Communication: UNIX supports communication methods using the write command, mail command, etc.
- Process Tracking: UNIX maintains a record of the jobs that the user creates. This function improves system performance by monitoring CPU usage. It also allows you to keep track of how much disk space each user uses, and the use that information to regulate disk space.
Today, UNIX is widely used in enterprise-level computing, scientific research, and web servers. Many modern operating systems, including Linux and macOS, are based on UNIX or its variants.

Figure – System Structure
- Layer-1: Hardware: It consists of all hardware related information.
- Layer-2: Kernel: This is the core of the Operating System. It is a software that acts as the interface between the hardware and the software. Most of the tasks like memory management, file management, network management, process management, etc., are done by the kernel.
- Layer-3: Shell commands: This is the interface between the user and the kernel. Shell is the utility that processes your requests. When you type in a command at the terminal, the shell interprets the command and calls the program that you want. There are various commands like cp, mv, cat, grep, id, wc, nroff, a.out and more.
- Layer-4: Application Layer: It is the outermost layer that executes the given external applications.
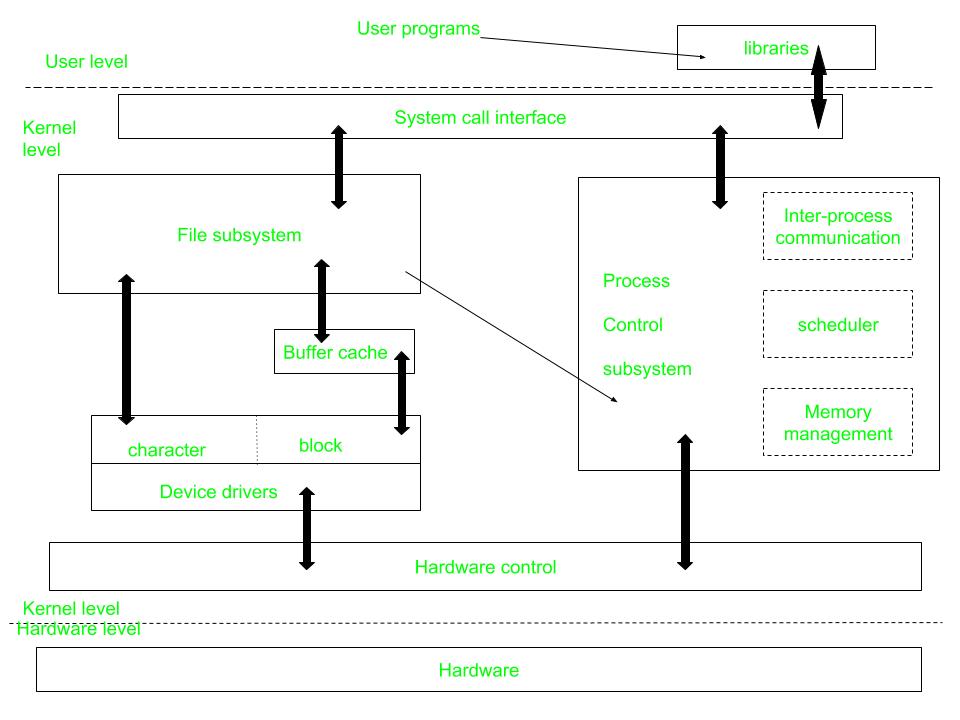
Figure – Kernel and its Block Diagram
This diagram shows three levels: user, kernel, and hardware.
- The system call and library interface represent the border between user programs and the kernel. System calls look like ordinary function calls in C programs. Assembly language programs may invoke system calls directly without a system call library. The libraries are linked with the programs at compile time.
- The set of system calls into those that interact with the file subsystem and some system calls interact with the process control subsystem. The file subsystem manages files, allocating file space, administering free space, controlling access to files, and retrieving data for users.
- Processes interact with the file subsystem via a specific set of system calls, such as open (to open a file for reading or writing), close, read, write, stat (query the attributes of a file), chown (change the record of who owns the file), and chmod (change the access permissions of a file).
- The file subsystem accesses file data using a buffering mechanism that regulates data flow between the kernel and secondary storage devices. The buffering mechanism interacts with block I/O device drivers to initiate data transfer to and from the kernel.
- Device drivers are the kernel modules that control the operator of peripheral devices. The file subsystem also interacts directly with “raw” I/O device drivers without the intervention of the buffering mechanism. Finally, the hardware control is responsible for handling interrupts and for communicating with the machine. Devices such as disks or terminals may interrupt the CPU while a process is executing. If so, the kernel may resume execution of the interrupted process after servicing the interrupt.
- Interrupts are not serviced by special processes but by special functions in the kernel, called in the context of the currently running process.
Difference B etween Unix and Linux
Linux is essentially a clone of Unix. But, basic differences are shown below:
Advantages of UNIX
- Stability: UNIX is known for its stability and reliability. It can run for long periods of time without requiring a reboot, which makes it ideal for critical systems that need to run continuously.
- Security: UNIX has a robust security model that includes file permissions, user accounts, and network security features. This makes it a popular choice for systems that require high levels of security.
- Scalability: UNIX can be scaled up to handle large workloads and can be used on a variety of hardware platforms.
- Flexibility: UNIX is highly customizable and can be configured to suit a wide range of needs. It can be used for everything from simple desktop systems to complex server environments.
- Command-line interface: UNIX’s command-line interface allows for powerful and efficient interaction with the system.
Disadvantages of UNIX
- Complexity: UNIX can be complex and difficult to learn for users who are used to graphical user interfaces ( GUIs ).
- Cost: Some UNIX systems can be expensive, especially when compared to open-source alternatives like Linux.
- Lack of standardization: There are many different versions of UNIX, which can make it difficult to ensure compatibility between different systems.
- Limited software availability: Some specialized software may not be available for UNIX systems.
- Steep learning curve: UNIX requires a certain level of technical knowledge and expertise, which can make it challenging for novice users.
Example of UNIX Command
# List files in a directory with detailed information ls -l
This command shows a detailed list of files and directories, including permissions of the logged in user, number of links, owner name, owner group, file size, and timestamp thoroghly.
The UNIX operating system continues to be a milestone in the today’s changing world of computing due it robustness, security, and flexibility. Its influence is seen in many and various operating systems, and its principles remain relevant as well as robust for understanding how an opereating systems works under the hood. By learning the UNIX , users can gain a valuable skill set including network security, cyber security , various file systems not only NTFS but also xfs, btrfs, ext4 etc. which is going to help user in many it Environment including Docker, kubernetes etc.

Frequently Asked Questions on UNIX System – FAQs
What are the main features of unix.
UNIX is known for it’s multiuser capability, multitasking, portability, security and hierarchial file system. This makes it out of the box versatality and powerful operating system.
How does UNIX handle security?
UNIX uses permission based system to control the access to the files and processes, ensuring that the users must and can only perform actiins they are authorized to do.
What is the difference between UNIX and Linux?
UNIX is the original operating system which is developed in the 1970s, while linux is a unix-like operating system created in the early 1990s. LInux is open-source and has a broader range of distributions like Debian, Ubuntu, Red Hat and etc.
Can UNIX be used on personal computers?
Yes, UNIX can and must be used as a personal computers. There are various versions of UNIX that are compatible with different types of hardware, including the Personal computers(PCs).
Similar Reads
- Computer Organization and Architecture
- Computer Subject
- Operating Systems Questions
Improve your Coding Skills with Practice
What kind of Experience do you want to share?
Browse Course Material
Course info.
- Dr. Katrina LaCurts
Departments
- Electrical Engineering and Computer Science
As Taught In
- Computer Design and Engineering
- Computer Networks
- Operating Systems
- Software Design and Engineering
Learning Resource Types
Computer system engineering, week 1: operating systems part i, recitation 1: worse is better.
- Read “ The Rise of Worse is Better ” by R. Gabriel and be prepared to discuss it.
Lecture 1: Coping with Complexity: Enforced Modularity via Client/server Organization
Lecture 1 outline.
- Introduction to Systems
- Why is Complexity Bad?
- Mitigating Complexity
- Enforced Modularity
- Other Goals
- Detailed Outline
Lecture Slides
- Lecture 1 Slides: Coping with Complexity (PDF)
- Book sections 1.1-1.5 and 4.1-4.3
Recitation 2: We Did Nothing Wrong
- Read “ We Did Nothing Wrong: Why Software Quality Matters ” by D. Gage & J. McCormick in Baseline Magazine on March 4, 2004
- We Did Nothing Wrong Assignment
Tutorial 1: Introduction to 6.033 Communication
Most of these tutorials will teach the communication theory and practices of this course, and assist you in preparing for the assignments. You’ll become fluent in a variety of communication genres, develop strategies and skills needed to present technical concepts to different audiences, learn how to use writing to develop and deepen your technical understanding—and get specific, directed instruction on writing and presenting your 6.033 assignments. A handful of the tutorials will be dedicated to discussing the design project.
System Critique Assignment 1: Evaluate and Assess a Domain Name System (DNS)
- Assigned: Critique Assignment 1

You are leaving MIT OpenCourseWare

IMAGES
VIDEO
COMMENTS
This contains the instructions and questions for the UNIX assignment 1 on "The UNIX Time-Sharing System" by Dennis Ritchie and Ken Thompson.
Learn the essential Linux/Unix commands you need to know with this cheat sheet. Includes commands for file management, permissions, environment variables, users, networking, processes, and more.
Describe the Linux architecture and common Linux distributions and update and install software on a Linux system. Perform common informational, file, content, navigational, compression, and networking commands in Bash shell.
Unix commands are entered at the command prompt in a terminal window, and they allow users to perform a wide variety of tasks, such as managing files and directories, running processes, managing user accounts, and configuring network settings.
This assignment also serves a second purpose: to ensure you are familiar with the Duke environment, including the Duke Linux cluster and the Sakai assignment submission facility. A note on the two environments you’ll be using. ents you’ll be exposed to here. In Part 1, you’ll create your own Ubuntu Linux virtual machine (VM) in th.
What does the UNIX shell do? How does it work? Why is it useful? As always, there are multiple correct answers for each of these questions. This contains the instructions and questions for the UNIX assignment 2.
The goals for this assignment are for you to get familiar with working in the Unix environment, and editing/building/running C programs. Unix and C Resources. The pages in the Handouts dropdown above have information, including videos, for various Unix commands, tools, and more that we'll be using this quarter.
To create a new variable, use the assignment operator ‘=‘. [username@scc1 ~]$. foo=“this is foo’s value”. The foo variable can be printed with echo. [username@scc1 ~]$ echo $foo this is foo’s value. To make $foo visible to programs run by the shell (i.e., make it an “environment variable”), use export:
UNIX is an innovative or groundbreaking operating system which was developed in the 1970s by Ken Thompson, Dennis Ritchie, and many others at AT&T Laboratories. It is like a backbone for many modern operating systems like Ubuntu, Solaris, Kali Linux, Arch Linux, and also POSIX.
System Critique Assignment 1: Evaluate and Assess a Domain Name System (DNS) Assigned: Critique Assignment 1. This section provides materials for Week 1: Operating Systems Part I . Materials include lecture outlines, slides, and readings as well as recitation and assignment activities.