
ISO/IEC 30107-3:2017 establishes:
- principles and methods for performance assessment of presentation attack detection mechanisms;
- reporting of testing results from evaluations of presentation attack detection mechanisms;
- a classification of known attack types (in an informative annex).
Outside the scope are:
- standardization of specific PAD mechanisms;
- detailed information about countermeasures (i.e. anti-spoofing techniques), algorithms, or sensors;
- overall system-level security or vulnerability assessment.
The attacks considered in this document take place at the sensor during presentation. Any other attacks are considered outside the scope of this document.

General information
- Status : Withdrawn Publication date : 2017-09 Stage : Withdrawal of International Standard [ 95.99 ]
- Edition : 1 Number of pages : 33
- Technical Committee : ISO/IEC JTC 1/SC 37 ICS : 35.240.15
- RSS updates
- ISO/IEC 30107-3:2017
- 00 Preliminary
- 10.99 2014-08-19 New project approved
- 20 Preparatory
- 30.00 2015-08-04 Committee draft (CD) registered
- 30.20 2015-09-16 CD consultation initiated
- 30.60 2015-11-18 Close of comment period
- 30.99 2016-03-02 CD approved for registration as DIS
- 40.00 2016-08-15 DIS registered
- 40.20 2016-10-13 DIS ballot initiated: 12 weeks
- 40.60 2017-01-06 Close of voting
- 40.99 2017-03-06 Full report circulated: DIS approved for registration as FDIS
- 50.00 2017-04-06 Final text received or FDIS registered for formal approval
- 50.20 2017-05-31 Proof sent to secretariat or FDIS ballot initiated: 8 weeks
- 50.60 2017-07-28 Close of voting. Proof returned by secretariat
- 60.00 2017-07-28 International Standard under publication
- 60.60 2017-08-23 International Standard published
- 90.92 2019-09-19 International Standard to be revised
- 95.99 2023-01-10 Withdrawal of International Standard
ISO/IEC 30107-3:2023

Got a question?
Check out our Help and Support
- Standards catalogue
Add to cart
Liveness Detection Certification, FIDO Certification and PAD Evaluations
Process & standards for certified liveness detection.

The following sections are geared at enabling corporates in need for a PAD solution to estimate the informative value of a liveness detection certification.
After reading this article you will know:
- The context and history of liveness detection certifications
- The process for receiving a certified liveness detection
- Different levels of presentation attacks
- How biometric anti-spoofing performance is measured
- The limitations of liveness detection certification
ISO Compliant Presentation Attack Detection
The knowledge for this article is based on BioID’s experience with two different types of liveness detection certifications: BioID has performed a PAD evaluation with the German testing laboratory TÜV Informationstechnik GmbH (TÜViT). The audit confirms the ISO 30107-3 compliance of BioID’s presentation attack detection technology. The FIDO accredited biometric laboratory TÜViT tested against criteria based on FIDO Biometric Certification Requirements v1.1 (FIDO1.1) and ISO/IEC 30107-3:2017 (ISO/IEC30107-3). The applied criteria are considered by TÜViT to be stricter than FIDO1.1, so as the test was successful, the FIDO criteria are also regarded as being met. In addition, ARIADNEXT, a long-term BioID customer, offers an identity verification solution which has been certified with a FIDO biometric component certification in November 2020. This solution includes BioID’s liveness detection for fraud prevention. It’s reliability was thoroughly tested during the FIDO testing procedures in 2020.
The ISO standard ISO/IEC 30107-3 for presentation attack detection was introduced in September 2017. This norm has been incorporated in the official FIDO certification process. Also, it has led to independent laboratories offering PAD evaluations based on this ISO norm. If a certified liveness detection is based on this ISO standard ISO/IEC 30107-3, there is a certain element of comparability between the different evaluations. Still, it is important to take a closer look at the testing protocols and results as various laboratories or test centers differ in how they carry out the performance assessment. This can result in disparity of the informative value of liveness detection certifications . Due to limited test scenarios, results might not be transferable to real-life scenarios. Hence, it may always be recommended to perform individual performance assessment before deciding for an anti-spoofing solution .
How Liveness Detection Certification Works
A biometric vendor trying to offer a certified liveness detection needs to engage with one of the accredited laboratories and provide a software/hardware solution for evaluation. The small number of accredited laboratories to perform a liveness detection certification include e.g. the German TÜV IT, the Swiss Center for Biometrics Research and Testing (Idiap Research Institute) and the French ELITT/Leti CEA. A full list of accredited test centers can be found in the resources list below.
For offering a certified liveness detection, biometric vendors can either choose to perform a FIDO certification or do a mere PAD evaluation. In addition to the PAD performance, a FIDO certification also includes the biometric verification (facial recognition) performance. During both performance tests, biometric anti-spoofing systems are challenged with different presentation attacks such as printed photos, paper masks or videos. If successfully tested according to ISO/IEC 30107-3, the biometric vendor receives a testing report (in the case of a PAD evaluation) or a FIDO certificate (if a full FIDO certification is performed).
Which Presentation Attacks are Tested
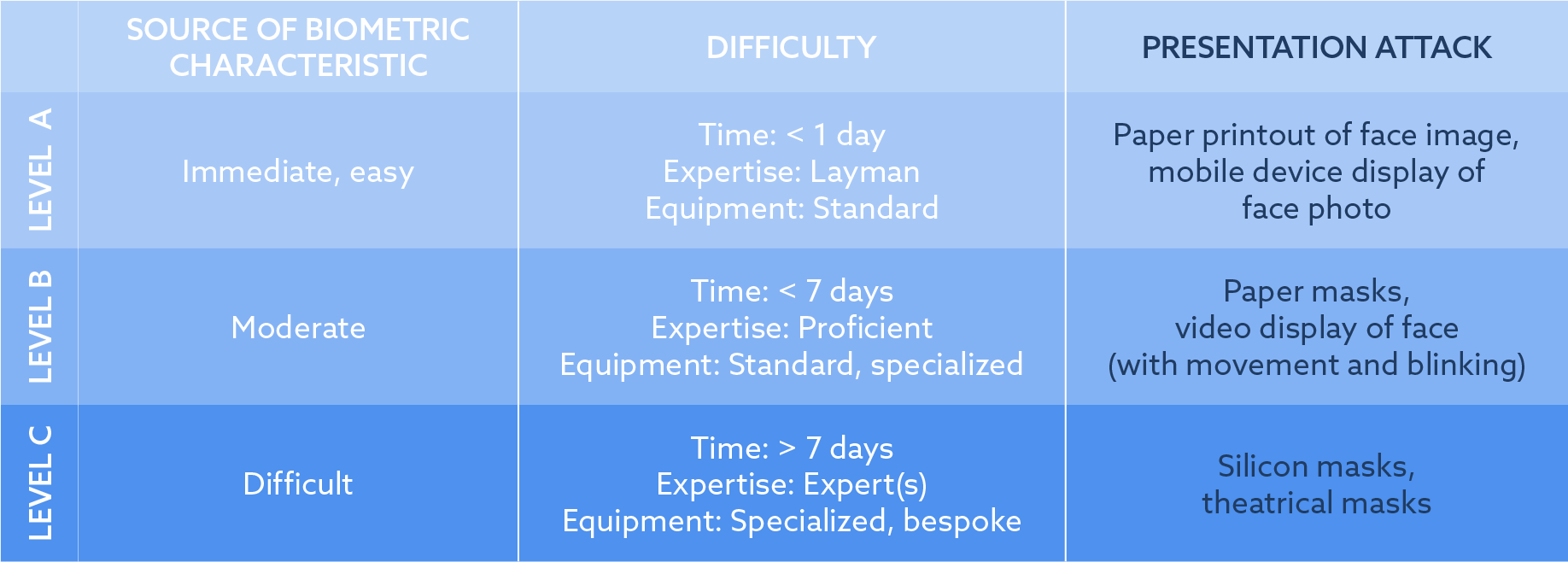
According to FIDO Biometrics Requirements published in 06/2019, there are three levels of presentation attack scenarios which can be tested against. These differ mainly in the time, expertise and equipment needed to create the attack (see table 1). Level A includes simple photo printouts, or a photo presented on a smartphone display, whereas level B additionally includes paper masks or videos of a person. Level C represents silicon masks, as well as high-quality videos of a person presented on a high-resolution display, for instance. Each of these attack examples is called a presentation attack instrument (PAI) . The testing is made with classes of attacks, the so called PAI species. Such a PAI species can be an iPhone 8 display presenting photos of various people. Another example of a PAI species are photos of different people printed on the same paper with the same printer. PAD evaluations can be made for each of the levels A-C separately. For a FIDO certification, an algorithm needs to detect spoofing attempts on levels A and B by default.
How Certified Liveness Performance is Measured
For a certified liveness detection, certain values are calculated to assess the performance: APCER (Attack Presentation Classification Error Rate) and BPCER (Bona-fide Presentation Classification Error Rate). APCER calculates the proportion of attacks mistakenly being classified as live persons. BPCER represents the proportion of live persons (also called Bona-fide) being classified as fakes. For mere PAD evaluation, no verification performance takes place. It is only tested whether a presented face came from a live person or not. For a full FIDO certification, the value calculated also includes the verification (facial recognition) result, resulting in IAPMR (Impostor Attack Presentation Match Rate). This number describes the proportion of attacks by impostors incorrectly accepted as the real person.
For receiving a certified liveness detection included in a FIDO certification, 10 presentation attack species (6 from level A and 4 from level B, see table 1) as well as 10 people (subjects) are needed. This results in 100 PAI. Each has a maximum of 5 attempts to spoof the liveness detection. In other words, 50 attempts per species, or 500 spoofing attempts are used altogether. In order to successfully complete this part of the performance testing, the IAPMR needs to be less than 20 % per PAI species, meaning less than 10 of the 50 attempts per species may wrongly be classified as a live person. For more details please see FIDO’s PAD criteria . In order to provide the desired objective performance measurement, liveness detection certifications that are not part of a FIDO certification process should be designed similarly.
Limitations of Liveness Detection Certifications
To be precise, there is no certification for presentation attack detection available on the market, as the international standard for PAD, ISO/IEC 30107-3, does not offer a standardized testing protocol which could be used to perform comparable testing and certification. As a consequence, there is no certified liveness detection solution available on the market, either. Instead, biometric testing laboratories like TÜViT from Germany or Idiap from Switzerland can perform evaluations based on the ISO standard and thus confirm a technology’s ISO compliance. Still, the term ‘certification’ or ‘certified liveness detection’ has been widely used. This has sometimes happened in a misleading way as the following article by a leading Professor at Clarkson University and at Biometrics Institute describes: Go to the Biometric Update article .
There are certain limitations of liveness detection certifications, which should be kept in mind when using them as decision criterion. For instance, for a PAD evaluation that is independent from FIDO, the vendor himself can choose and decide the level of PAI, the number of attacks and the number of subjects. Even for a strongly regulated FIDO certification, the number of devices and spoofing scenarios tested is limited. This should be kept in mind as the biometric anti-spoofing can perform differently on unseen presentation attacks. Also, when reviewing the test reports of evaluated/certified solutions, there are details which should be looked at closely, for instance, the false rejection of live people (BPCER). This calculation is often kept unmentioned as there is a direct link between APCER and BPCER: if the solution is designed to perform extremely well on APCER (correctly rejecting fakes), this can result in a higher BPCER (falsely rejecting live people). In a real-world scenario, of course, this has to be balanced in order to create security and usability at the same time.
Compliant Presentation Attack Detection
As a German biometrics company with more than 20 years of experience in the market, BioID sees with great interest how the biometrics industry is changing. With its multiple patents, BioID is a leading player worldwide to offer software-based biometric anti-spoofing. As the demand for facial recognition is growing, the market has seen many new entrants and a broad diversification of offerings. As such, standards like the ISO/IEC 30107-3 offer guidelines for an objective measurement for presentation attack detection performance. For a buying decision, while a liveness detection certification does facilitate the assessment process, one must pay attention to their intended application by considering factors such as ease of integration, user experience, as well as vendor credibility (e.g. in terms of GDPR). Every application scenario is different and the best way to find a suitable anti-spoofing solution is to find a trusted & experienced vendor.
BioID Liveness Detection can be tested and evaluated at the BioID Playground . For integration of our Web-APIs into your services, please request a free trial instance . Contact us for more information.
Resources on Liveness Detection Certification
- For more information on FIDO Biometric Component Testing please see: https://fidoalliance.org/certification/biometric-component-certification/
- FIDO Biometrics Requirements; Final Document, June 06, 2019: https://fidoalliance.org/specs/biometric/requirements/
- ISO/IEC 30107-3:2017 Information technology — Biometric presentation attack detection — Part 3: Testing and reporting: https://www.iso.org/standard/67381.html
- Link to accredited test laboratories: https://fidoalliance.org/certification/biometric-component-certification/fido-accredited-biometric-laboratories/
Ann-Kathrin Freiberg +49 911 9999 898 0 [email protected]
Standards for Biometric Presentation Attack Detection
- First Online: 02 January 2019
Cite this chapter

- Christoph Busch 6
Part of the book series: Advances in Computer Vision and Pattern Recognition ((ACVPR))
2173 Accesses
5 Citations
This chapter reports about the relevant international standardization activities in the field of biometrics and specifically describes standards on presentation attack detection that have established a framework including a harmonized taxonomy for terms in the field of liveness detection and spoofing attack detection, an interchange format for data records and moreover a testing methodology for presentation attack detection. The scope and of the presentation attack detection multipart standard ISO/IEC 30107 is presented. Moreover, standards regarding criteria and methodology for security evaluation of biometric systems are discussed.
This is a preview of subscription content, log in via an institution to check access.
Access this chapter
Subscribe and save.
- Get 10 units per month
- Download Article/Chapter or eBook
- 1 Unit = 1 Article or 1 Chapter
- Cancel anytime
- Available as PDF
- Read on any device
- Instant download
- Own it forever
- Available as EPUB and PDF
Tax calculation will be finalised at checkout
Purchases are for personal use only
Institutional subscriptions
Similar content being viewed by others

Introduction to Presentation Attack Detection in Fingerprint Biometrics


Related Standards
International Civil Aviation Organization NTWG: machine readable travel documents – Part 4 – specifications for machine readable passports (MRPs) and other TD3 size MRTDs (2015). http://www.icao.int/publications/Documents/9303_p4_cons_en.pdf
ISO/IEC JTC1 SC37 Biometrics: ISO/IEC 19794-1:2011 Information technology - biometric data interchange formats – Part 1: framework (2011). International organization for standardization
Google Scholar
ISO/IEC JTC1 SC37 Biometrics: ISO/IEC 19794-4:2011 Information technology – biometric data interchange formats – Part 4: finger image data (2011). International organization for standardization
ISO/IEC JTC1 SC37 Biometrics: ISO/IEC 19794-5:2011. Information technology - biometric data interchange formats – Part 5: face image data (2011). International organization for standardization
ISO/IEC JTC1 SC37 Biometrics: ISO/IEC 2382-37 harmonized biometric vocabulary (2017). International organization for standardization
ISO/IEC JTC1 SC37 Biometrics: ISO/IEC 2382-37 harmonized biometric vocabulary (2017). http://www.christoph-busch.de/standards.html
ISO/IEC JTC1 SC37 Biometrics: ISO/IEC SC37 SD11 general biometric system (2008). International organization for standardization
ISO/IEC TC JTC1 SC37 Biometrics: ISO/IEC 19784-1:2006. Information technology – biometric application programming interface – Part 1: bioAPI specification (2006). International organization for standardization
Zwiesele A, Munde A, Busch C, Daum H (2000) Biois study - comparative study of biometric identification systems. In: IEEE computer society, 34th annual 2000 IEEE international carnahan conference on security technology (CCST), pp 60–63
Matsumoto T, Matsumoto H, Yamada K, Yoshino S (2002) Impact of artificial “Gummy” fingers on fingerprint systems. In: SPIE conference on optical security and counterfeit deterrence techniques IV, vol 4677, pp 275–289
Schuckers SA (2002) Spoofing and anti-spoofing measures. In: Information security technical report 4, Clarkson University and West Virginia University, USA
Article Google Scholar
Raghavendra R, Busch C (2017) Presentation attack detection methods for face recognition systems: a comprehensive survey. ACM Comput Surv 50(1):8:1–8:37. https://doi.org/10.1145/3038924
Galbally J, Gomez-Barrero M (2016) A review of iris anti-spoofing. In: 4th international conference on biometrics and forensics (IWBF), pp 1–6
Sousedik C, Busch C (2014) Presentation attack detection methods for fingerprint recognition systems: a survey. IET Biom 3(1):1–15
ISO/IEC JTC1 SC37 Biometrics: ISO/IEC 30107-1. Information technology - biometric presentation attack detection – Part 1: framework (2016). International organization for standardization
ISO/IEC JTC1 SC37 Biometrics: ISO/IEC 30107-2. Information technology - biometric presentation attack detection – Part 2: data formats (2017). International organization for standardization
ISO/IEC JTC1 SC37 Biometrics: ISO/IEC 30107-3. Information technology - biometric presentation attack detection – Part 3: testing and reporting (2017). International organization for standardization
Ellingsgaard J, Busch C (2017) Altered fingerprint detection. Springer International Publishing, Cham, pp 85–123. https://doi.org/10.1007/978-3-319-50673-9_5
Chapter Google Scholar
ISO/IEC JTC1 SC37 Biometrics: ISO/IEC 29794-1:2016 information technology - biometric sample quality – Part 1: framework (2016). International organization for standardization
ISO/IEC JTC1 SC37 Biometrics: ISO/IEC 19795-1:2017. Information technology – biometric performance testing and reporting – Part 1: principles and framework (2017). International organization for standardization and international electrotechnical committee
Mansfield T, Wayman J (2002) Best practices in testing and reporting performance of biometric devices. CMSC 14/02 Version 2.01, NPL
Criteria C (2012) Common methodology for information technology security evaluation - evaluation methodology. http://www.commoncriteriaportal.org/cc/
Download references
Author information
Authors and affiliations.
Hochschule Darmstadt and CRISP (Center for Research in Security and Privacy), Haardtring 100, 64295, Darmstadt, Germany
Christoph Busch
You can also search for this author in PubMed Google Scholar
Corresponding author
Correspondence to Christoph Busch .
Editor information
Editors and affiliations.
Idiap Research Institute, Martigny, Switzerland
Sébastien Marcel
University of Southampton, Southampton, UK
Mark S. Nixon
Universidad Autonoma de Madrid, Madrid, Spain
Julian Fierrez
EURECOM, Biot Sophia Antipolis, France
Nicholas Evans
Rights and permissions
Reprints and permissions
Copyright information
© 2019 Springer Nature Switzerland AG
About this chapter
Busch, C. (2019). Standards for Biometric Presentation Attack Detection. In: Marcel, S., Nixon, M., Fierrez, J., Evans, N. (eds) Handbook of Biometric Anti-Spoofing. Advances in Computer Vision and Pattern Recognition. Springer, Cham. https://doi.org/10.1007/978-3-319-92627-8_22
Download citation
DOI : https://doi.org/10.1007/978-3-319-92627-8_22
Published : 02 January 2019
Publisher Name : Springer, Cham
Print ISBN : 978-3-319-92626-1
Online ISBN : 978-3-319-92627-8
eBook Packages : Computer Science Computer Science (R0)
Share this chapter
Anyone you share the following link with will be able to read this content:
Sorry, a shareable link is not currently available for this article.
Provided by the Springer Nature SharedIt content-sharing initiative
- Publish with us
Policies and ethics
- Find a journal
- Track your research

Meet Us at GITEX Africa

- Press Release
Buyers Guide
Complete playbook to understand liveness detection industry
What is APCER (Attack Presentation Classification Error Rate)?
On June 6th, 2024, the FATE Morph research publication by NIST entitled NISTIR 8292 DRAFT SUPPLEMENT was updated. This testing is regularly carried out on facial recognition solutions to analyze their performance in presentation attack detection like face morphing . Two primary quantities; APCER & BPCER are reported that are the determinants of the accuracy and robustness of a facial recognition tool.
In this knowledge base, we will explain the first quantity metric i.e. APCER.
What is APCER?
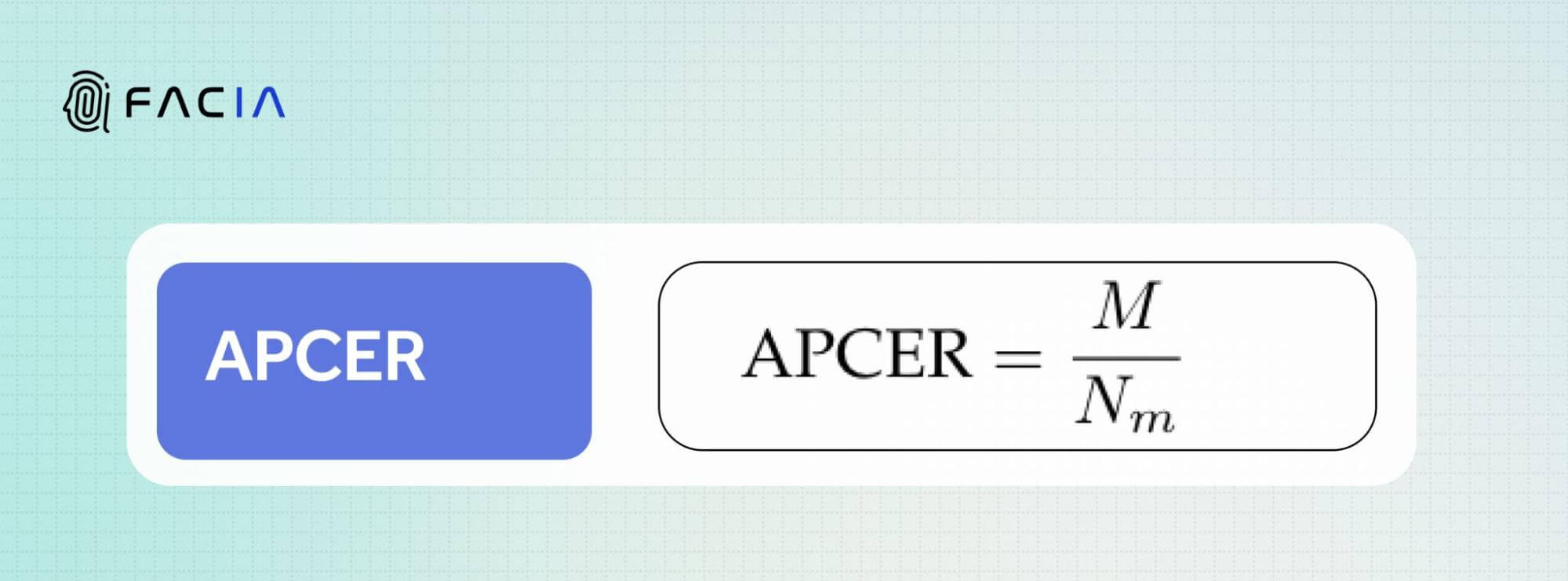
APCER is an acronym for Attack Presentation Classification Error Rate which is defined as the frequency of a biometric facial recognition tool with which it wrongly accepts a biometric presentation attack as a genuine face presentation. It is also termed the ‘Morph Miss Rate’ in NIST research and testing publications.
How is APCER Calculated?
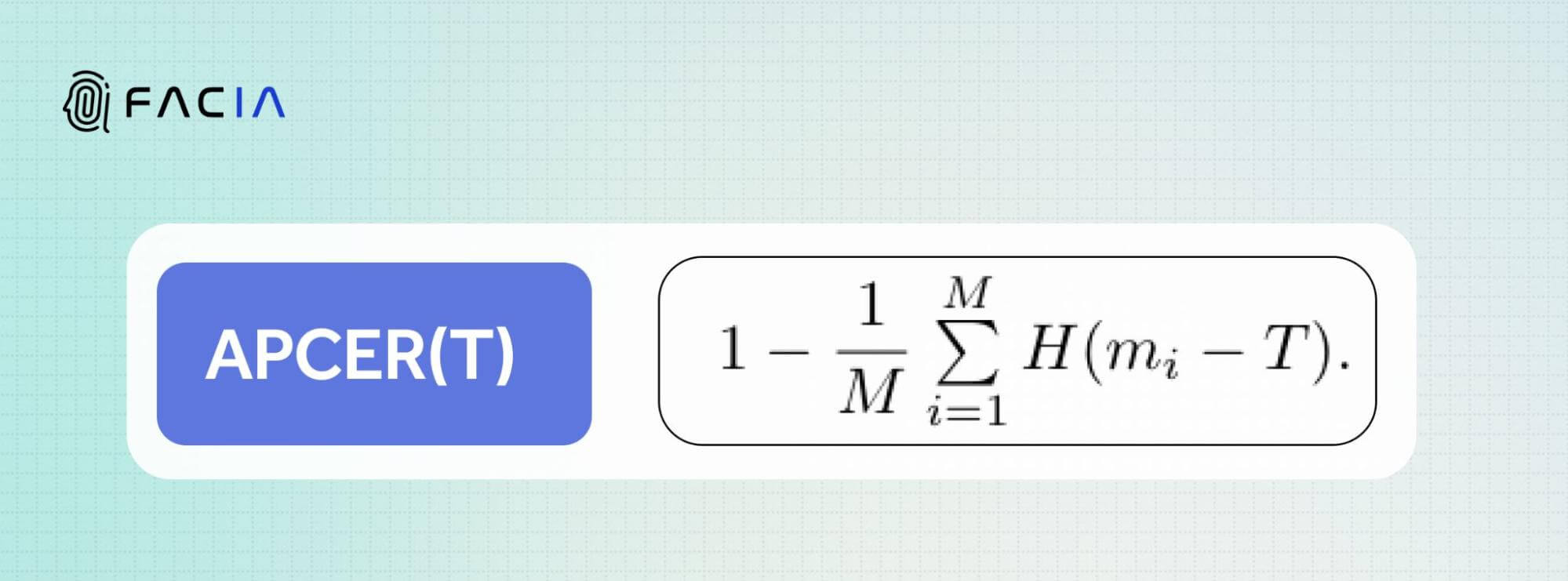
It is calculated in the following equation:
The number of morph images wrongly classified as bona fide images is divided by the total number of actual morph attack images.
APCER vs. BPCER
As per NIST findings, it is not possible to calculate APCER alone until and unless:
- A Presentation Attack Image curation is completed
- BPCER values are set, fixed & kept below such as:
- APCER @ BPCER = 0.01 in Fate Morph Detection (For Face Morphing and Impersonation attacks)
- APCER @ BPCER = 0.0001 in FRVT PAD API (for all other Presentation attack types)
What is the Ideal APCER?
Based on the above set value, APCER values are calculated for different biometric identity solution providers by NIST.
Look at the statistical explanation of APCER’s calculation above a threshold below:
Here is the analytical summary of APCER in biometrics values under different image sets presented to the algorithm tested by NIST :
Single-Image Morphing Detection
A single image (morphed or bona fide) is presented to the algorithm.
Here are the summarized results:
From the above findings, it is clear that few biometric system algorithms have achieved 0.000 APCER under specific conditions. However, the dataset contains 22 algorithmic submissions under each data set and tier. This shows that solutions need to improve their accuracy levels to minimize presentation attack acceptance rate.
A further summary of test results related to APCER vs. BPCER is given in the knowledge piece of BPCER .
Impact of APCER Value in Biometric Facial Recognition
It is evident that if APCER in biometrics is high there is a high chance of identity theft attempts going undetected resulting in bigger threats like:
- Account Takeover fraud
- Financial scams
- Crypto fraud and theft
- Money Laundering
It is important to keep the face presentation attack detection in place by using an AI-powered facial recognition solution that is compliant with NIST standards in achieving the lowest possible error rates. For this purpose, the facial recognition tool must be regularly tested on NIST metrics with improvements in algorithms to reach a perfect zero. In this way, the solution will become spoof-proof for Biometric PAD (Presentation Attack Detection) using facial recognition. Moreover, the solutions need to improve their liveness detection feature to ensure the prevention of presentation attacks & their error rates well before time.
RELATED BLOGS

20 Nov 2024
Cheap Fakes vs Deep Fakes–Rising Identity Fraud Threats in the Digital Age
Imagine that the friend you are talking to is...

15 Nov 2024
KOSPA ACT–Parent’s Guide to Protecting Kids Online from Unsafe Content
Kids are extremely exposed to a variety of online...

08 Nov 2024
Evolving Use Cases, Market Trends, & Innovations in Face Authentication
Face authentication is a biometric technology created to ensure...
Search Blog
Recent Posts
Digital Identity Verification a Safer EKYC Step Against Deepfake Attacks
Related Blogs
- Privacy Policy
- Terms of Use

IMAGES
VIDEO
COMMENTS
Attack presentation non-response rate (APNRR) proportion of presentation attacks that cause no response at the PAD subsystem or data capture subsystem • Bona Fide presentation non-response rate (BPNRR) proportion of bona fide presentations that cause no response at the PAD subsystem or data capture subsystem ‣
BPCER (Bona fide Presentation Classification Error Rate) is the false detection of a genuine user image as a fake one. Read this detailed Knowledge base about BPCER.
One-Class Classifiers ØAdapt classifiers such as SVMs or Gaussian Mixture Models (GMMs) to be trained only on bona fide data IFPC 2020, PAD and UnknownAttacks, 28/10/2020 13 Anomalydetection Marta Gomez-Barrero O. Nikisins, A. Mohammadi, A. Anjos, S. Marcel, "On effectiveness of anomaly detection approaches against unseen
•Impostor attack presentation match rate (IAPMR) in a full-system evaluation of a verification system, the proportion of impostor attack presentation using the same PAI species in which the target reference is matched •Concealer attack presentation non-match rate (CAPNMR) in a full-system evaluation of a verification system, the
- principles and methods for performance assessment of presentation attack detection mechanisms; - reporting of testing results from evaluations of presentation attack detection mechanisms; - a classification of known attack types (in an informative annex). Outside the scope are: - standardization of specific PAD mechanisms;
Generally, most of those approaches consider attack detection as a bi-class classification problem where classifiers are trained on both bona fide presentations (BPs) and attack presentations. ...
Liveness Detection Certification, FIDO Certification and PAD Evaluations Process & Standards for Certified Liveness Detection . Also known as presentation attack detection (PAD), liveness detection certification and certified liveness detection solutions have become the hot topic of the whole biometrics industry. In the following, this article will thus explain the most important elements of a ...
Impostor attack presentation match rate (IAPMR) • Impostor attack presentation accept rate (IAPAR) in a full-system evaluation of a verification system, proportion of impostor presentation attacks using the same PAI species that result in a accept . Christoph Busch . Standardisation on PAD 2016. Presentation Attack Detection - Testing. 24
This chapter reports about the relevant international standardization activities in the field of biometrics and specifically describes standards on presentation attack detection that have established a framework including a harmonized taxonomy for terms in the field of liveness detection and spoofing attack detection, an interchange format for data records and moreover a testing methodology ...
The number of morph images wrongly classified as bona fide images is divided by the total number of actual morph attack images. APCER vs. BPCER As per NIST findings, it is not possible to calculate APCER alone until and unless: